1. What is OWASP?
Why Every Developer Should Know About OWASP
Let’s face it—building secure apps isn’t easy. There’s always a new vulnerability around the corner, and hackers are getting smarter every day.
That’s where OWASP steps in.
Meet OWASP: Your Security Best Friend
OWASP stands for the Open Worldwide Application Security Project. It’s a non-profit foundation focused on improving the security of software. Think of it as a giant open-source toolkit built by real security professionals, developers, and researchers from around the world.
And the best part?
It’s completely free.
Yes, free to use, free to share, and free to learn from.
What Makes OWASP So Trustworthy?
OWASP is not just any group shouting about security online.
It’s backed by thousands of industry experts, volunteers, and organizations who live and breathe cybersecurity.
Their work is well-respected in the tech industry — from startups to giants like Microsoft and Google.
So when you see OWASP guidelines or tools mentioned in security checklists or job interviews, now you know:
It matters. A lot.
What Does OWASP Actually Do?
Here’s what OWASP offers (for free!):
- Security Tools: Useful tools like ZAP (a web vulnerability scanner).
- Learning Materials: Guides, books, cheat sheets—great for beginners and pros.
- Community Projects: Dozens of open-source projects you can join or learn from.
- Events & Conferences: They host local meetups and global conferences where you can connect and learn directly from experts.
Why Should You Care About OWASP?
Whether you’re a developer, tester, or tech enthusiast, OWASP helps you:
✅ Write safer code
✅ Understand real-world vulnerabilities
✅ Protect your apps from cyberattacks
✅ Build trust with users and clients
It’s not about scaring you—it’s about empowering you to build things the right way.
What is the OWASP Top 10?
The Security Cheat Sheet Every Developer Needs
If you build web apps—or work with someone who does—you need to know the OWASP Top 10.
Why? Because it’s like a must-read safety manual for writing secure code.
The OWASP Top 10 isn’t just a list.
It’s an awareness standard. Trusted by developers, cybersecurity experts, and companies around the world.
Understanding the OWASP Top 10
Every few years, OWASP analyzes data from real-world security breaches and research across thousands of apps.
Then they publish a list of the Top 10 most critical web application security risks.
This helps:
✅ Developers know what to avoid
✅ Teams set security priorities
✅ Businesses reduce risk early in the development cycle
Let’s explore each of the Top 10 — explained simply.
1. Broken Access Control
When users get access they shouldn’t.
Let’s say a regular user can somehow access the admin dashboard. Or download someone else’s private file.
That’s Broken Access Control.
It happens when rules aren’t properly enforced.
Attackers love this, because it gives them access to data or functions they shouldn’t see.
🖼️ [Insert Image: Diagram showing user bypassing role-based restrictions — caption: “Example of a user bypassing role access controls.”]
2. Cryptographic Failures
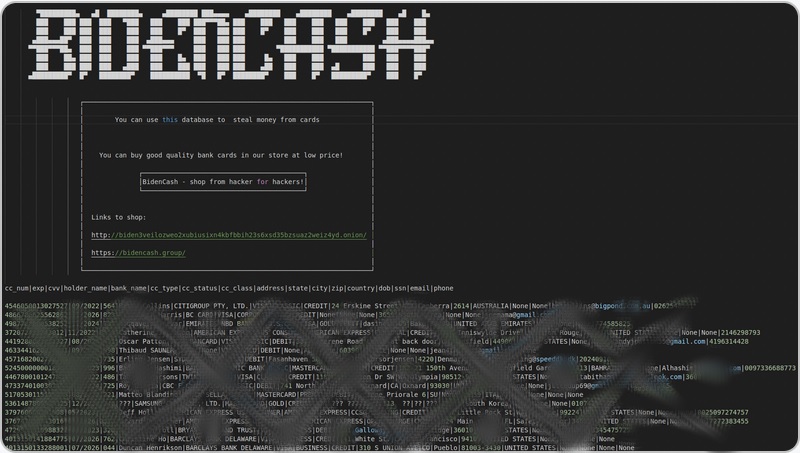
Weak encryption = easy data theft.
Imagine a website stores passwords in plain text or uses outdated encryption methods.
That’s a cryptographic failure.
It’s like locking your door but leaving the key under the mat.
Always use strong, updated encryption standards and store sensitive data securely.
3. Injection
When the app takes malicious input literally.
For example:
A login form accepts input directly into a database. An attacker types in special characters instead of a username—and boom! They can view or change database records.
This is called SQL Injection.
Others include NoSQL, OS command, and LDAP injection.
4. Insecure Design
When security isn’t baked into the blueprint.
Sometimes, the app’s architecture or workflow is fundamentally unsafe.
It might lack input validation, proper authentication flow, or session timeout.
Insecure design means the app was flawed from the start.
Fixing it later is harder—so secure design needs to happen early in development.
5. Security Misconfiguration
When default settings leave the door wide open.
Examples:
- Using the default admin password
- Forgetting to disable debug mode
- Leaving unused ports or services open
These missteps give attackers an easy way in.
6. Vulnerable and Outdated Components
Old libraries can be a hacker’s best friend.
If your app relies on outdated frameworks or plugins with known bugs, it’s at risk.
Even popular tools can have vulnerabilities if you don’t keep them updated.
Example:
Running an old version of jQuery or Log4j without the security patch? Big mistake.
7. Identification and Authentication Failures
When logging in isn’t as secure as it should be.
This includes:
- Weak or guessable passwords
- No multi-factor authentication (MFA)
- Session IDs that can be stolen or guessed
It’s like leaving the front door unlocked and expecting no one to try it.
8. Software and Data Integrity Failures
When your app trusts the wrong source.
Let’s say you install a plugin from a third-party site without checking its source.
Or your CI/CD pipeline automatically deploys updates without verification.
If any part of that chain is tampered with, attackers can inject malicious code into your app.
9. Security Logging and Monitoring Failures
If no one sees the breach, did it even happen?
Without proper logging, you may not even realize you’ve been hacked.
Monitoring and alerting help detect breaches early.
This gives teams time to respond before things spiral out of control.
10. Server-Side Request Forgery (SSRF)
When the server trusts the wrong URLs.
With SSRF, attackers trick your server into making requests—often to internal systems that shouldn’t be exposed.
Example:
Your app fetches a profile image from a URL. The attacker enters http://localhost/admin, and the server unknowingly makes the request.
This can expose sensitive internal data.