Understanding the Mirai IoT Botnet
Introduction to IoT Botnets
The Internet of Things (IoT) has revolutionized the way we interact with technology, connecting everyday devices like cameras, thermostats, and refrigerators to the internet. While this connectivity offers convenience, it also introduces significant security vulnerabilities.
One of the most notorious examples of exploiting these vulnerabilities is the Mirai botnet, which harnessed the power of compromised IoT devices to launch massive cyberattacks.
What is an IoT Botnet?
An IoT botnet is a network of internet-connected devices infected with malicious software and controlled as a group without the owners’ knowledge. These devices, often with minimal security measures, can be co-opted to perform coordinated tasks such as Distributed Denial of Service (DDoS) attacks, data theft, or spam distribution. The Mirai botnet exemplifies the potential scale and impact of such networks.
The Rise of IoT Devices and Security Gaps
The proliferation of IoT devices has outpaced the implementation of robust security protocols. Many devices are shipped with default usernames and passwords, which users often neglect to change. Additionally, manufacturers may not provide regular software updates, leaving devices vulnerable to known exploits. These security gaps create an environment ripe for exploitation by malware like Mirai.
Origins of the Mirai Botnet
The Mirai botnet emerged in 2016, developed by three college students: Paras Jha, Josiah White, and Dalton Norman. Initially intended to gain an advantage in the Minecraft gaming community by overwhelming competitors’ servers, Mirai quickly evolved into a tool capable of launching unprecedented DDoS attacks. The creators released the source code publicly, leading to widespread adoption and adaptation by other malicious actors.
Timeline of Mirai’s Initial Attacks
- September 2016: Mirai launched a 620 Gbps DDoS attack on cybersecurity journalist Brian Krebs’ website, overwhelming its defenses.
- October 2016: A significant attack on Dyn, a DNS provider, disrupted access to major websites like Twitter, Netflix, and Reddit across the U.S. and Europe.
- November 2016: The botnet targeted Deutsche Telekom, affecting nearly a million customers in Germany.
These attacks highlighted the vulnerabilities inherent in IoT devices and the potential for widespread disruption.

How the Mirai Botnet Works
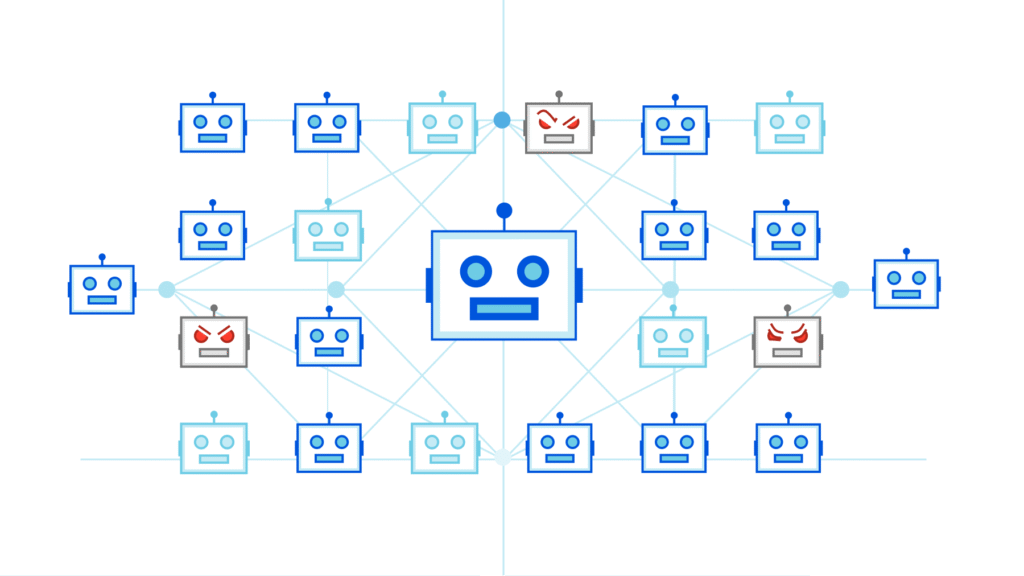
Mirai operates by scanning the internet for IoT devices with open Telnet ports (23 and 2323) and attempting to log in using a list of common default credentials. Once access is gained, the malware infects the device, turning it into a “bot” that can receive commands from a central server. The botnet can then be directed to launch DDoS attacks, overwhelming targeted servers with traffic.
Default Credentials Exploitation
A critical factor in Mirai’s success was its exploitation of default credentials. Many IoT devices are shipped with factory-set usernames and passwords, such as “admin/admin” or “user/1234,” which users often fail to change. Mirai’s hardcoded list of over 60 such credentials allowed it to rapidly compromise a vast number of devices.
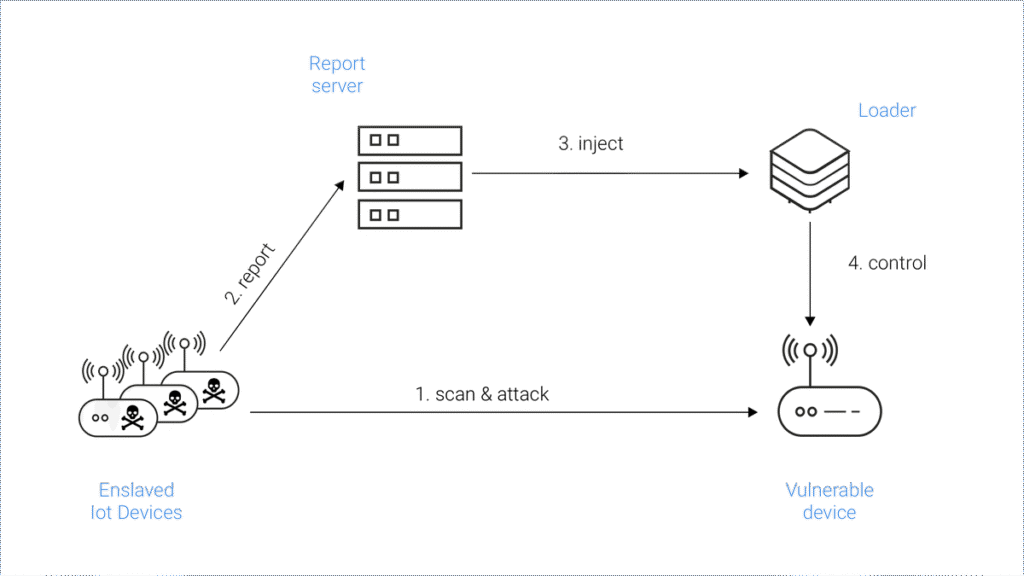
Command and Control (C&C) Infrastructure
Infected devices communicate with a Command and Control (C&C) server, which issues instructions for scanning, infection, and launching attacks. This centralized control structure enables coordinated actions across the botnet. Some variants of Mirai have adopted decentralized models to evade detection and takedown efforts.
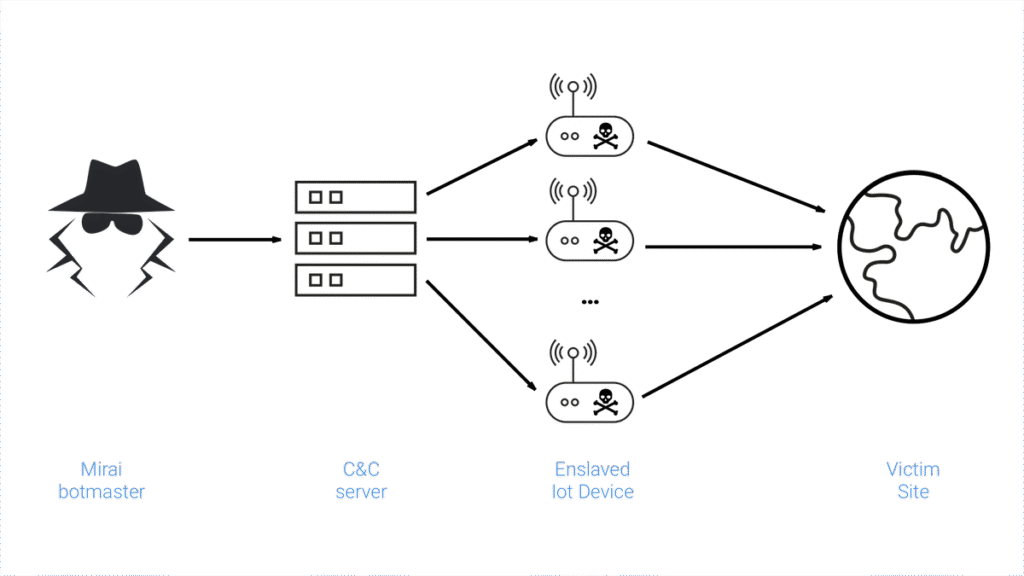
Major Attacks Launched by Mirai
- Dyn DNS Attack: The October 2016 attack on Dyn disrupted access to major websites, highlighting the botnet’s capacity to impact critical internet infrastructure.
- OVH Attack: French hosting provider OVH was targeted with a DDoS attack exceeding 1 Tbps, one of the largest recorded at the time.
- Liberia Internet Disruption: Repeated attacks effectively took the entire country’s internet offline, demonstrating the botnet’s global reach.
Technical Anatomy of Mirai
Mirai’s codebase is relatively simple and modular, written in C for the bot and Go for the controller. Its lightweight design allows it to run on devices with limited processing power. The malware includes components for scanning, brute-force login attempts, and executing various types of DDoS attacks, such as TCP, UDP, and HTTP floods.
Propagation Techniques
Mirai spreads by continuously scanning IP ranges for devices with open Telnet ports. Upon finding a target, it attempts to log in using its list of default credentials. Successful logins result in the device being infected and added to the botnet. The malware also removes competing malware and disables remote administration to maintain control over the device.
Botnet Lifecycle Management
The lifecycle of a Mirai-infected device includes:
- Infection: The device is compromised through brute-force login attempts.
- Reporting: The bot reports to the C&C server and receives instructions.
- Execution: The device participates in scanning, infection, or DDoS attacks.
- Persistence: The malware remains in the device’s memory until a reboot.
- Reinfection: If the device is rebooted without changing credentials, it can be quickly reinfected.
Variants and Evolution of Mirai
Since the release of its source code, numerous Mirai variants have emerged, each with unique features:
- Satori: Exploits specific vulnerabilities in Huawei routers.
- Okiru: Targets devices with ARC processors.
- Masuta: Focuses on routers with weak security configurations.
These variants demonstrate the adaptability of Mirai’s code and the ongoing threat it poses.
Global Impact and Case Studies
- Deutsche Telekom Incident: In November 2016, an attempt to infect routers with Mirai disrupted internet service for approximately 900,000 customers in Germany.
- Financial Sector Attacks: In 2018, a Mirai variant targeted financial institutions, utilizing over 13,000 devices to generate significant traffic volumes.
These incidents underscore the botnet’s capacity to affect various sectors and geographies.
Legal Consequences and Creator Sentencing
The creators of Mirai were apprehended and pled guilty to charges related to computer fraud. As part of their sentencing, they cooperated with the FBI, assisting in cybersecurity efforts and contributing to the development of tools to combat similar threats. Their case highlights the potential for rehabilitation and the importance of leveraging technical expertise in cybersecurity defense.
Mitigation Strategies and Best Practices
To protect against threats like Mirai:
- Change Default Credentials: Immediately update factory-set usernames and passwords on all devices.
- Regularly Update Firmware: Ensure devices have the latest security patches.
- Network Segmentation: Isolate IoT devices from critical systems.
- Disable Unused Services: Turn off unnecessary features like Telnet.
- Monitor Network Traffic: Use intrusion detection systems to identify unusual activity.
Implementing these measures can significantly reduce the risk of infection.
The Ongoing Threat of IoT Botnets
Despite increased awareness, many IoT devices remain vulnerable due to poor security practices. As the number of connected devices grows, so does the potential for exploitation. Continuous vigilance, user education, and industry-wide standards are essential to mitigate the risks posed by botnets like Mirai.
Conclusion
The Mirai botnet serves as a stark reminder of the vulnerabilities inherent in the rapidly expanding IoT landscape. Its ability to compromise vast numbers of devices and launch large-scale attacks underscores the need for robust security measures. By understanding the mechanisms of such threats and implementing proactive defenses, individuals and organizations can better protect themselves in an increasingly connected world.
FAQs
Q1: How can I tell if my IoT device is infected with Mirai?
A1: Signs include sluggish device performance, unexpected reboots, or unusual network traffic. Monitoring tools can help detect anomalies.
Q2: Does rebooting my device remove Mirai?
A2: Yes, Mirai resides in volatile memory and is removed upon reboot. However, if default credentials remain unchanged, the device can be reinfected quickly.
Q3: Are all IoT devices vulnerable to Mirai?
A3: Devices with default or weak credentials and open Telnet ports are particularly at risk. Regular updates and strong passwords enhance security.
Q4: Can antivirus software protect against Mirai?
A4: Traditional antivirus solutions may not be effective on IoT devices. Network-level security measures and proper device configuration are more effective.
Q5: What should manufacturers do to prevent such botnets?
A5: Manufacturers should enforce secure default settings, provide regular firmware updates, and educate users on best security practices.