Imagine searching for help on Facebook, Netflix, or Microsoft, and being tricked into calling a fake support number. That’s exactly what just happened.
Cybercriminals have hijacked how legitimate websites display content by injecting fake phone numbers into their search results and pages. This new twist on an old scam is catching users off-guard, and it’s happening on some of the biggest platforms in the world.
What Really Happened?
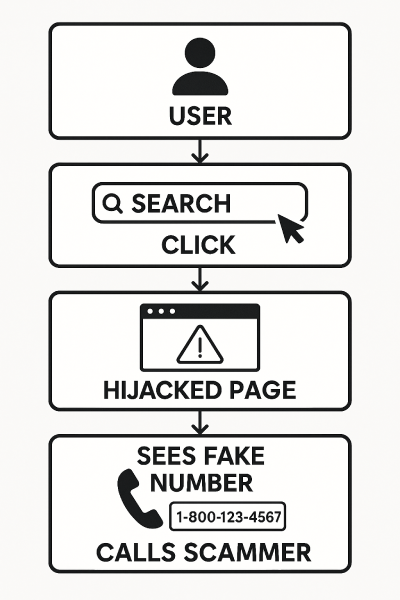
Security researchers have uncovered a clever abuse of search parameters, those little text strings you see in a website’s URL after you run a search.
For example:https://facebook.com/search?q=support
What hackers realized is that many sites, including Facebook, Netflix, and Microsoft, don’t properly sanitize or validate this user input. That means if someone tweaks the URL, they can make arbitrary text, like a phone number, show up on the page.
Attackers began exploiting this by inserting fraudulent customer service numbers into these search results. When unsuspecting users looked for help, they’d often see these hijacked pages in Google search results… and believe them to be legitimate.
Why This Is So Dangerous
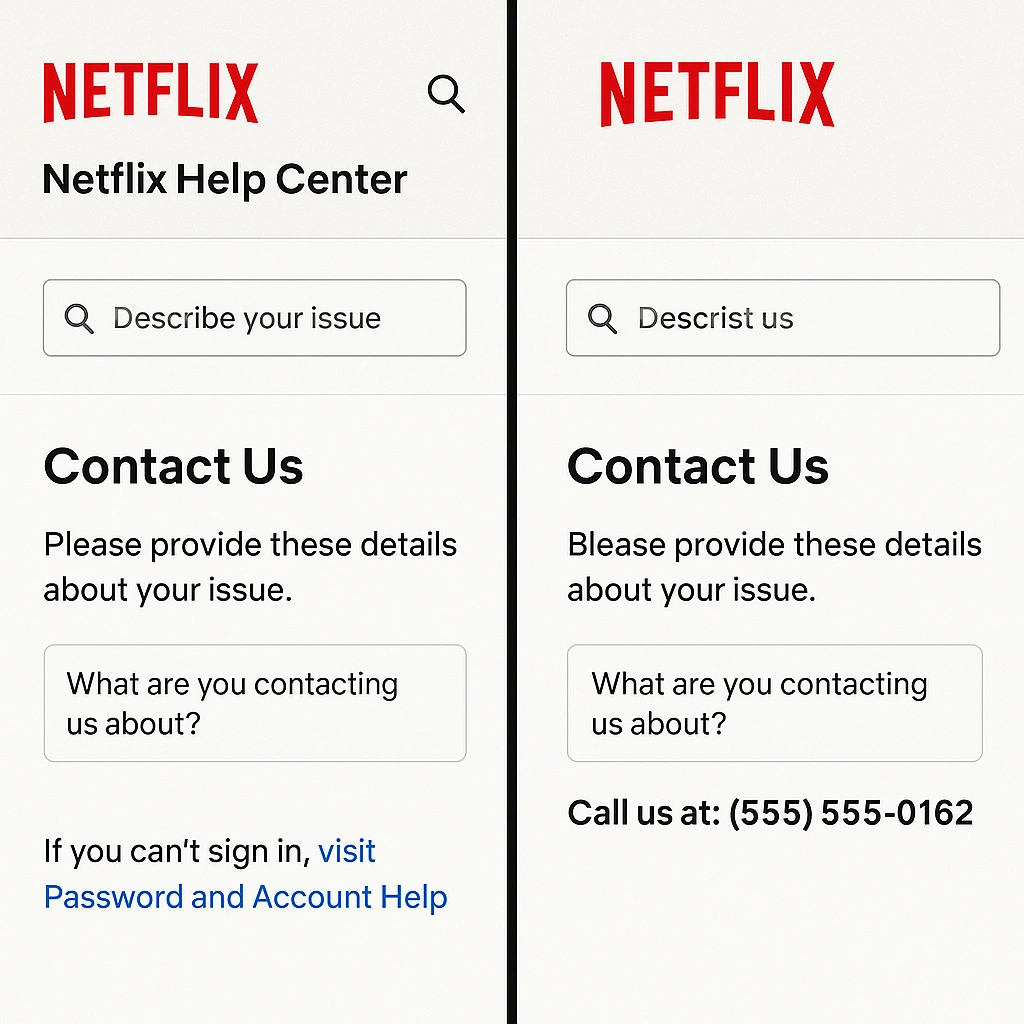
Let’s say you’re having trouble with your Netflix login. You search online for “Netflix customer support,” and you click on what looks like a legit Netflix link. The page even has the official Netflix layout, logo, and branding, but there’s a fake phone number prominently listed.
When you call it, you’re connected to a scammer who pretends to be a Netflix agent. They might say:
- “We’ve noticed suspicious activity on your account.”
- “We need to verify your billing info to reactivate your service.”
- “Please install a support tool so we can fix your issue remotely.”
These scams can lead to:
- Stolen credit card info
- Malware installed on your system
- Loss of account access
- Data breaches at a personal level
Who’s Behind This?
This isn’t your average script kiddie attack. These appear to be organized threat actors or SEO scammers using a technique known as Search Parameter Injection. It’s part of a broader trend where attackers manipulate how web content is rendered, without ever breaching the site itself.
In many cases, attackers embed their own content (fake numbers, phishing links) into legitimate URLs. These manipulated URLs are then indexed by Google or Bing, making them look trustworthy when users search for help.
And since the base domain is still “facebook.com” or “microsoft.com,” most users don’t suspect a thing.
What Are Facebook, Microsoft, and Netflix Doing About It?
At the time of writing, there hasn’t been a direct public statement from the affected companies. But security experts are urging these platforms to:
- Sanitize all input fields, especially in URL parameters
- Prevent user-generated text from rendering unescaped
- Implement WAF rules to detect injection attempts
This incident is drawing comparisons to past search parameter abuse cases, such as Google’s search redirect exploits and Apple tech support scams.
How You Can Protect Yourself
This kind of scam can trick even tech-savvy users. Here’s how to stay safe:
- Never trust support numbers shown in search results. Always go to the official website.
- Don’t call numbers from pop-ups or third-party sites.
- Use verified apps or portals to access customer service (e.g., Netflix app, Microsoft account).
- Report suspicious content to the company directly.
- Enable Two-Factor Authentication (2FA) to prevent account takeover.
The Bigger Lesson: Website Security Still Has Gaps
What this shows is that even tech giants are vulnerable if input isn’t sanitized properly. Search parameter injection is a low-tech, high-impact attack that can affect any site with dynamic content.
And here’s the kicker: the websites aren’t technically “hacked.” The attack happens through the front door, via poorly handled search strings and dynamic content rendering.
This is a wake-up call for web developers and cybersecurity teams everywhere. You don’t need a zero-day to wreak havoc. Sometimes, a simple unchecked URL is all it takes.
FAQs – What People Are Asking
What is a Search Parameter Injection Attack?
It’s when attackers insert text (like fake phone numbers) into a site’s search URL to make that content appear on a legitimate page.
Are Facebook, Netflix, and Microsoft actually hacked?
No. Their websites weren’t breached. The attackers exploited how the sites display user-generated text.
Is it dangerous to call these numbers?
Yes! You may be speaking to scammers trying to steal your personal or financial data.
How can I verify a support number is real?
Always visit the company’s official Help or Contact page—not just what you find on search engines.
Final Thoughts
This incident is a powerful reminder that even trusted websites can be misused in creative and malicious ways. Cybercriminals are getting more sophisticated, and they know how to manipulate search behavior, URL structures, and user trust.
The best defense? Awareness, education, and vigilance.
As users, we must double-check before we click or call. And as developers, it’s time to close these loopholes, because small cracks lead to big damage.