How These Hidden Flaws Could Hand Over Your Entire System to Hackers
1. The Silent Power Grab Happening Inside Your Linux System
They’re In, and You Don’t Even Know It — How Local Bugs Become Full-Blown Breaches
Most people think of hackers breaking in from the outside.
But what if they don’t have to?
In many Linux systems, attackers don’t need to find a remote backdoor — they just wait for someone to log in normally… then use hidden bugs to escalate their privileges and take over the system completely.
In this article, we’ll walk you through:
- What privilege escalation actually is
- How these attacks work
- Real-world vulnerabilities
- How you can detect, prevent, and defend against them
2. What Is Privilege Escalation in Linux? (And Why Should You Care?)
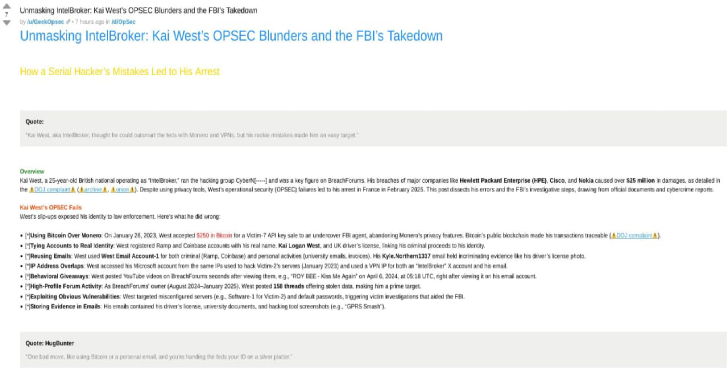
From Nobody to God — How Hackers Hijack the ‘Root’ of Your System
In simple terms, privilege escalation means gaining access rights that you’re not supposed to have.
For example:
- A regular user suddenly runs commands that only the root user should be able to
- A hacker who breaks into a web server account can turn that into full control of the machine
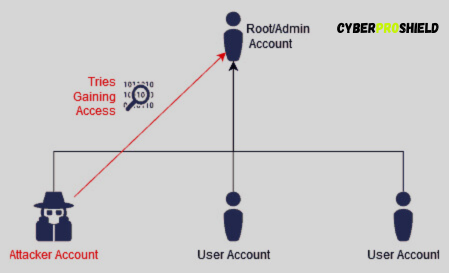
There are two types:
- Vertical escalation: Going from low privileges to higher (like from user to root)
- Horizontal escalation: Moving sideways (like from one user to another)
Why it matters: Once an attacker has root access, they can:
- Read and write any file
- Install malware or backdoors
- Hide their activity
- Compromise every user on the system
3. How Attackers Pull It Off: Real Tactics They Use
Inside the Hacker’s Toolkit — How They Break the Rules (and Win Big)
Here’s how attackers typically pull off privilege escalation:
Common techniques include:
- Exploiting SUID binaries: Programs with special root permissions that weren’t configured safely
- Cron job abuse: Scheduled tasks that run with elevated permissions
- Kernel exploits: Bugs in the Linux kernel that give away root access
- PATH variable manipulation: Replacing trusted system commands with malicious ones
- Misconfigured services: Weak settings that allow overreach
Real-world example: Attackers have used Dirty Pipe (CVE‑2022‑0847) to overwrite read-only files and gain root access — all from a local, unprivileged shell.
4. Notable Linux Vulnerabilities That Grant Root Access
Cracks in the Foundation — These Bugs Can Break Your Entire System
Examples include:
- CVE‑2024‑53141: Memory corruption issue in the Linux kernel — allows attackers to run arbitrary code with root privileges
- CVE‑2025‑21756: A use-after-free flaw in
vsockaffecting VMs and container systems - Dirty Pipe: A classic example of turning a read-only file into a writable attack surface
Why they’re dangerous: These bugs don’t need remote access. All it takes is local execution, which can happen after phishing, credential theft, or weak user controls.
5. What Happens After They Get Root? (And How You Can Tell)
You’ve Been Owned — But Could You Even Tell?
Once the attacker has root, the game changes. They can:
- Delete logs
- Create hidden users
- Install rootkits
- Exfiltrate sensitive data
Detection is possible, but tricky. Watch for:
- Unexpected users in the sudoers file
- Strange cron jobs or binaries in
/tmp,/var, or user folders - Logs showing UID 0 actions from unusual sessions
- Modifications to files like
/etc/shadowor/etc/passwd
Image Suggestion: Flowchart showing signs of root-level compromise post-exploitation.
6. Preventing Privilege Escalation — Think Beyond Patching
You Can’t Patch What You Can’t See — Here’s What Actually Works
Yes, patching is important, but it’s not enough.
Hardening strategies that actually make a difference:
- Use AppArmor or SELinux to control what users and processes can do
- Remove or audit SUID/SGID binaries
- Enforce strict sudo rules
- Disable unused services
- Monitor for file and permission changes
Special tip for containers and VMs: Use seccomp profiles, gVisor, or Kata containers to restrict system calls.
7. Patch Management and Prioritization Framework
Don’t Just Patch Fast — Patch Smart
Step 1: Prioritize Based on Exploitability
- Use sources like CISA KEV Catalog, ExploitDB, and Rapid7
- Patch vulnerabilities that have known exploits first
Step 2: Assess Business Impact
- Check if your systems are actually exposed or affected
- Use a risk matrix to prioritize based on your environment
Step 3: Scope and Rollout Plan
- Test patches in staging
- Automate with Ansible, Puppet, or Chef
- Create a weekly routine to avoid panic patching
Bonus Tip: Use vulnerability scanners like OpenVAS, Qualys, or Tenable
8. Detection Tools and Automation Workflows
Spot the Hack Before It Happens — Tools to See the Invisible
Recommended tools:
- LinPEAS: Finds local escalation paths
- pspy: Monitors hidden processes
- Auditd: Logs important system activity
- Falco: Real-time behavioral detection
- Chkrootkit/RKHunter: Detect rootkits and changes
Automation tips:
- Schedule LinPEAS scans
- Create Auditd rules for root/sensitive actions
- Use Falco with custom detection rules
9. Testing Your System’s Resilience
Hack Yourself First — Before Someone Else Does
Testing techniques:
- Run LinPEAS and Linux Exploit Suggester as a normal user
- Use GTFOBins to test misuse of SUID binaries
- Use pspy to uncover hidden activity
Create a resilience scoreboard:
| Category | Risk Found? | Fix Applied? |
|---|---|---|
| SUID Binaries | Yes | ✅ Done |
| Kernel Exploit | No | N/A |
| Unprotected Cron Jobs | Yes | ✅ Hardened |
10. Real-World Incident: From Exploit to Root Access
One Slip — Total Takeover: A Hacker’s Privilege Escalation in Action
Scenario walkthrough:
- Access: Attacker uses leaked SSH key
- Scan: Runs LinPEAS, finds Dirty Pipe
- Exploit: Executes PoC, gains root
- Persistence: Creates hidden user and cron job
- Cleanup: Deletes logs, hides activities
Mapped to MITRE ATT&CK:
| Phase | MITRE Technique |
|---|---|
| Initial Access | Valid Accounts (T1078) |
| Discovery | System Info Discovery (T1082) |
| Privilege Escalation | Exploitation for Priv Esc (T1068) |
| Persistence | Scheduled Task (T1053) |
| Defense Evasion | Clear Command History (T1070.003) |
11. Final Thoughts: Don’t Just Patch — Prepare
Secure the Root of the Problem — Before Hackers Do
Privilege escalation isn’t a theoretical risk — it’s how attackers gain full control. You need more than patches:
Final checklist:
- Scan regularly with LinPEAS
- Patch high-risk CVEs based on threat intel
- Harden permissions, SUIDs, and services
- Use real-time detection tools
- Test your systems like an attacker would
- Monitor root activity continuously
Let this guide be your blueprint to detect, defend, and defeat privilege escalation threats before they root your systems from the inside out.