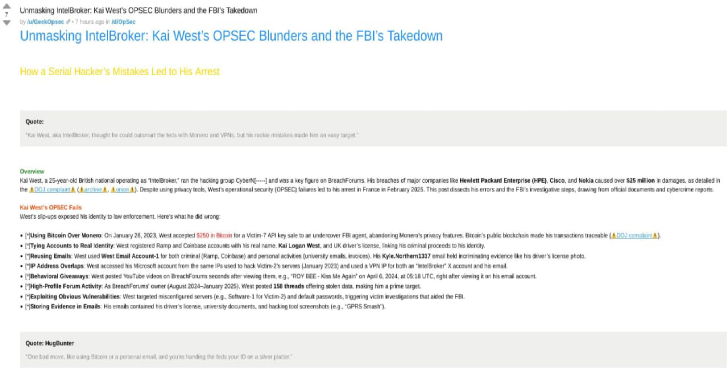
In today’s hyper-connected digital world, preventing hacking is not just a technical concern—it’s a business imperative. Cyber threats have evolved, and so must your defenses. As cybersecurity risks grow, businesses and individuals alike must employ proactive and advanced strategies to secure their systems, data, and digital assets.
Understanding the Threat Landscape
Hackers no longer fit the stereotype of lone individuals working in the shadows. Today’s cybercriminals are part of organized, well-funded networks utilizing sophisticated tools to exploit vulnerabilities. From ransomware attacks to phishing schemes, their methods are becoming more advanced and widespread.
To prevent hacking, it’s crucial to understand the types of cyberattacks businesses and individuals face:
- Phishing and Social Engineering
- Ransomware and Malware
- SQL Injection
- Zero-Day Exploits
- DDoS Attacks
- Credential Stuffing
- Man-in-the-Middle Attacks (MITM)
Strengthen Your Password Policies
One of the most common entry points for hackers is weak or reused passwords. Enforcing robust password management can significantly reduce vulnerability.
Best Practices for Password Security:

- Use complex passwords that include upper and lowercase letters, numbers, and special characters.
- Avoid dictionary words or easily guessable information like birthdates or pet names.
- Change passwords regularly, especially for sensitive systems.
- Use password managers like LastPass or Bitwarden to generate and store secure passwords.
Enable Two-Factor Authentication (2FA)
Two-Factor Authentication adds an extra layer of security by requiring a second form of verification, such as a mobile code or biometric scan. This drastically reduces the risk of unauthorized access—even if credentials are stolen.
Implement 2FA for:
- Email accounts
- Banking and financial services
- Cloud storage
- Social media platforms
- Enterprise systems and admin dashboards
Keep All Software and Systems Updated
Outdated software is a goldmine for hackers. Developers regularly release patches and updates to fix vulnerabilities that can be exploited.
Update Strategies:
- Enable auto-updates on all operating systems, software, and applications.
- Use patch management tools like ManageEngine or Ivanti to automate system-wide updates.
- Regularly audit your systems to ensure everything is up-to-date and secure.
Install and Configure a Reliable Firewall

Firewalls act as the first line of defense, filtering incoming and outgoing traffic and blocking malicious content.
Types of Firewalls:
- Hardware firewalls (for enterprise networks)
- Software firewalls (built into operating systems)
- Next-Generation Firewalls (NGFWs) which include intrusion prevention systems (IPS) and deep packet inspection (DPI)
Set up custom rules based on your network’s structure and access controls to ensure only necessary traffic passes through.
Use Antivirus and Anti-Malware Software
Even the most secure networks can be compromised. Reliable antivirus and anti-malware software act as your safety net.
Recommended Solutions:
- Norton 360
- Bitdefender
- Malwarebytes
- Kaspersky
- ESET NOD32
Set these tools to run real-time protection and schedule daily scans for early detection and removal of threats.
Educate Employees and Raise Cyber Awareness
Human error remains one of the leading causes of cybersecurity breaches. All team members should be trained on best practices.
Topics for Cybersecurity Training:
- Identifying phishing emails
- Secure file sharing practices
- Safe internet browsing
- Avoiding public Wi-Fi for sensitive operations
- Reporting suspicious behavior or emails
Conduct regular mock phishing simulations and quizzes to reinforce learning.
Secure Your Wi-Fi Networks

Unsecured Wi-Fi is an open invitation for hackers.
Wi-Fi Security Tips:
- Use WPA3 encryption (or WPA2 at minimum)
- Change default router credentials
- Disable SSID broadcasting for private networks
- Use a separate guest network for visitors
- Regularly update router firmware
Backup Data Regularly and Securely
No system is foolproof. Backing up your data ensures that in the event of a breach or ransomware attack, your data can be restored quickly and efficiently.
Backup Strategy:
- Follow the 3-2-1 rule: 3 copies of data, 2 different media types, 1 off-site backup
- Automate backups with tools like Acronis or Veeam
- Store sensitive data in encrypted formats
Limit User Access and Permissions
Adopt the principle of Least Privilege (PoLP): give users only the access they need.
Benefits of PoLP:
- Reduces attack surface
- Prevents insider threats
- Minimizes damage in case of compromised credentials
Regularly audit user roles and permissions, and revoke access when it’s no longer needed.
Encrypt Sensitive Data
Encryption turns readable data into unreadable code, making it useless to hackers without the decryption key.
Encryption Tips:
- Use end-to-end encryption for messaging and file transfers
- Enable full-disk encryption on devices
- Protect databases using AES-256 encryption standards
- Always use HTTPS for websites to secure data in transit
Monitor Your Systems Continuously
Proactive monitoring can help detect anomalies before they turn into full-scale breaches.
Monitoring Tools:
- SIEM tools (e.g., Splunk, IBM QRadar)
- Network monitoring tools (e.g., SolarWinds, Nagios)
- Log analysis platforms (e.g., Loggly, ELK Stack)
Set up alerts for unusual login attempts, spikes in traffic, or unauthorized access requests.
Perform Regular Security Audits and Penetration Tests

Audits help uncover vulnerabilities that may have gone unnoticed. Conduct internal and external penetration testing using certified ethical hackers to simulate real-world attack scenarios.
Include in Your Audit:
- Code reviews
- Network scanning
- Configuration checks
- Access logs review
- Social engineering attempts
Stay Compliant with Regulations
Adhering to data privacy laws and cybersecurity regulations helps avoid hefty fines and demonstrates a commitment to user safety.
Key Compliance Standards:
- GDPR (for handling EU citizens’ data)
- HIPAA (for healthcare)
- PCI DSS (for credit card processing)
- ISO/IEC 27001 (for information security management)
Conclusion: Act Now, Stay Secure
Cyber threats are not a matter of if, but when. By following these best practices, you not only prevent hacking but also fortify your digital presence, safeguard sensitive data, and protect your reputation in an increasingly hostile online environment.
Don’t wait until it’s too late. Secure your systems, educate your teams, and invest in cybersecurity now.