Cybersecurity in Today’s Digital Age
In this digital era, in which the world has become a global village, protecting digital systems is more important than ever. With businesses relying on technology for everything from communication to transactions, even one small vulnerability can have massive consequences.
Fortinet’s Position in Network Protection
Fortinet is known for delivering top-tier security tools like firewalls and secure gateways. Their products are used by enterprises and governments alike. But like any software, vulnerabilities can still be discovered, and when they are, it’s critical to act fast.

What Is an OS Command Injection?
Defining the Threat
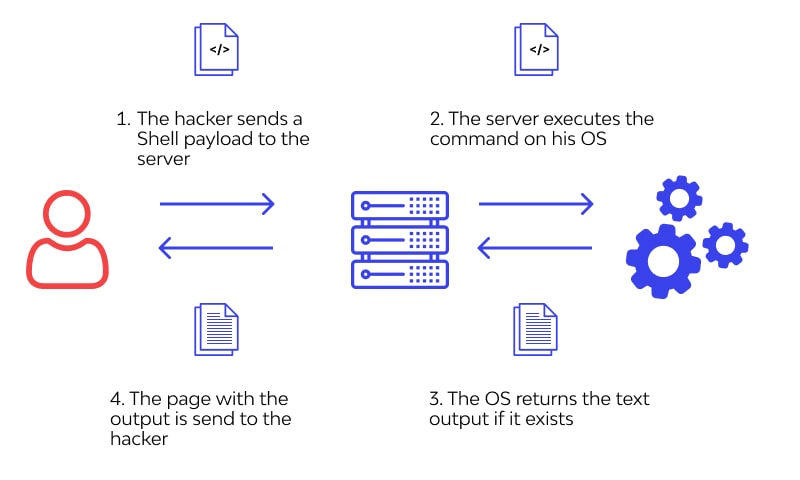
OS Command Injection is a type of cyber vulnerability where an attacker tricks an application into running system-level commands. It happens when input from users isn’t properly filtered and is passed directly to the operating system shell.
How It Functions
When software allows external input, like from a form or web request, and doesn’t properly sanitize it, attackers can insert commands. These get executed on the server just like a legitimate admin command.
Entry Points for Attackers
- Admin panels on web interfaces
- API endpoints with weak input checks
- Remote management tools
- Scripts with direct shell access
Indicators of Compromise
- Unrecognized users in the system
- Strange network traffic patterns
- Unexplained performance slowdowns
- Unexpected files or processes running
Inside the Fortinet Vulnerability
Which Fortinet Products Are Affected?
The flaw affected certain versions of FortiOS and FortiProxy, specifically versions with a web management interface that permitted unsafe command execution under specific conditions.
Technical Analysis of the Issue
The vulnerability, listed under CVE-2023-34992, stemmed from unsafe processing of user input in the web interface. If a logged-in user exploited it, they could execute commands on the host OS, essentially gaining deeper control of the device.
Why the Flaw Exists
It boils down to missing input validation. The system trusted data entered via the user interface without checking it properly, leading to unauthorized command execution paths.
Risk Assessment
This vulnerability received a critical risk rating, with a CVSS score nearing 9.3. That means it was easy to exploit and had a high impact on affected systems, making it extremely dangerous.
Evidence of Exploitation
How Hackers Take Advantage
Soon after the vulnerability became public, cybercriminals began scanning for Fortinet devices on the web. By using automated tools, they identified systems that hadn’t yet been patched, and exploited the flaw to plant malware or open backdoors.
Attack Groups and Tools Used
Groups linked to state-sponsored operations and organized cybercrime were seen exploiting this flaw. Security researchers tracked signs of APT (Advanced Persistent Threat) involvement, and tools like Metasploit modules were adapted quickly.
Consequences of the Exploit
Organizational Exposure
A compromised Fortinet device can act as a highway into the rest of your network. Hackers can:
- Bypass firewall protections
- Monitor traffic
- Steal sensitive information
- Deploy ransomware inside your organization
Financial and Operational Fallout
Besides data breaches, businesses may face:
- Huge regulatory fines
- Customer trust erosion
- Productivity loss
- System downtime costs
Detection and Fixes
Signs You’ve Been Targeted
Admins should watch for:
- Unexpected command execution logs
- Changes in firewall or routing rules
- Suspicious IPs accessing admin portals
- Abnormal user behavior patterns
Fortinet’s Patch and Advice
Fortinet responded by releasing a fix and issuing an advisory urging users to update affected products. Customers were advised to upgrade to the latest secure versions and restrict access to the web interface.
Safe Update Guidelines
- Always back up configuration data
- Test updates in a sandbox
- Follow Fortinet’s version-specific upgrade paths
- Monitor systems during and after updates
Workaround Methods
For users unable to patch right away:
- Disable the web management interface
- Use IP allowlisting
- Enforce 2FA and strong credentials
- Segment access to the management network
Long-Term Security Practices
Keep Your Systems Updated
Updates fix known flaws, it’s that simple. Automate updates where possible and stay informed through vendor security bulletins.
Watch Your Network Closely
Deploy monitoring tools to detect strange behavior. Set up alerts for failed login attempts, configuration changes, and traffic anomalies.
Educate Your Staff
Employees are often the weakest link. Teach them to recognize suspicious activity, avoid risky behavior, and report issues quickly.
What This Incident Teaches Us
Lessons for the Security Community
Even the most trusted brands can have vulnerabilities. This case highlights the importance of proactive testing, responsible disclosure, and fast patching.
The Need for Better Development Standards
Secure coding isn’t optional. Developers must use input validation, conduct code reviews, and implement security-by-design principles from day one.
Conclusion
The Fortinet OS Command Injection vulnerability is a reminder that no system is invincible. Whether it’s a firewall, router, or any other security device, a single flaw can put everything at risk. Staying secure isn’t just about having the right tools. It’s about using them wisely, keeping them updated, and staying ahead of threats before they become disasters.
FAQs
What role does Fortinet play in cybersecurity?
Fortinet provides security solutions like firewalls, VPNs, and intrusion detection systems for organizations around the world.
How dangerous is OS command injection?
It’s highly dangerous. Attackers can run system-level commands that give them control over servers or network devices.
What can I do to avoid such vulnerabilities?
Keep your software up to date, restrict access to critical interfaces, and monitor for suspicious activity regularly.
How fast did Fortinet respond?
Fortinet acted promptly by issuing patches and public advisories soon after the vulnerability was confirmed.
Is Fortinet still reliable after this?
Yes, as long as you’ve updated your devices. The key is regular maintenance and applying security updates without delay.











2 Comments
Thanks
Great post