A newly identified vulnerability in eSIM technology allows cybercriminals to duplicate digital SIM profiles and assume victims’ mobile identities. This method creates significant threats for both individuals and organizations, giving attackers access to calls, texts, authentication codes, and confidential data. As eSIM usage becomes more widespread, understanding this threat and implementing proper defenses is essential.
What Is eSIM and Why Does It Matter?
An eSIM (embedded SIM) is a virtual version of the traditional SIM card, integrated directly into a device’s hardware. Unlike physical SIMs, eSIM profiles can be remotely downloaded, activated, and switched, offering greater convenience and flexibility. They are commonly found in modern smartphones, tablets, wearables, and IoT devices.
How the New eSIM Attack Works
Overview of the Attack
- Profile Duplication: Hackers exploit flaws in the provisioning process to copy a user’s eSIM profile onto another device.
- Identity Takeover: Once cloned, the attacker’s device is treated as the original by mobile networks, allowing access to calls, messages, and 2FA codes.
- Remote Execution: Many of these attacks can be executed remotely, without any physical access to the victim’s device.
Technical Breakdown
- Provisioning Vulnerabilities: Weak authentication or lack of encryption during the activation process may allow attackers to capture or replay eSIM data.
- Social Engineering: Cybercriminals may deceive users or carrier support staff into initiating a profile transfer, much like SIM swap scams.
- Malicious Software: Malware installed on a compromised device may be used to extract and forward eSIM data to the attacker.
Potential Impact
- Account Compromise: Hackers can intercept verification codes, gaining unauthorized access to banking, email, and social media.
- Communication Breach: Sensitive phone calls and text messages can be intercepted or redirected.
- Fraud and Impersonation: Cloned profiles can be used for financial scams, identity theft, or corporate espionage.
- Loss of Access: Victims might lose control over their phone number or services if the original eSIM is deactivated.
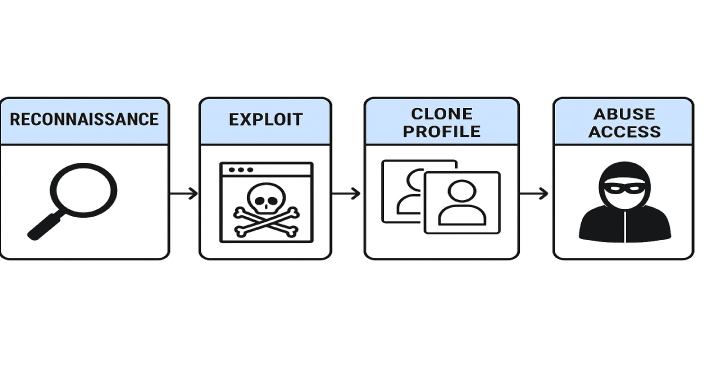
Step-by-Step Breakdown of the Attack
- Target Identification: The attacker gathers information about the victim such as phone number, device model, and carrier.
- Exploit or Manipulate Support: The attacker uses technical loopholes or deceives carrier support to initiate the transfer.
- Profile Cloning: The attacker acquires the victim’s eSIM data and loads it onto their own device.
- Identity Hijacking: The attacker’s device now receives all the victim’s communications.
- Abuse of Access: The attacker uses the access to compromise further accounts or conduct fraud.
How to Detect an Attack
- Unexpected Device Activity: Watch for unfamiliar eSIM activations or profile downloads.
- Loss of Connectivity: Sudden inability to make calls or receive texts may indicate an attack.
- Security Notifications: Alerts from services regarding new logins or password changes should be investigated promptly.

How to Prevent It
- Enhanced Authentication: Carriers must use strong multi-factor authentication for profile activations and transfers.
- User Awareness: Users should avoid sharing activation or QR codes and be cautious of phishing attempts.
- Secure Provisioning: Use encrypted channels and strict verification during eSIM provisioning.
- Carrier Monitoring: Telecom providers should actively monitor for unusual provisioning activity and flag anomalies.
- Device Protection: Keep software up to date and avoid installing untrusted applications that could access eSIM data.
Frequently Asked Questions
| Question | Answer |
|---|---|
| What is eSIM profile cloning? | It refers to copying a digital SIM profile onto another device for misuse. |
| How is this different from SIM swap? | eSIM cloning can be executed remotely, while SIM swapping typically involves social engineering or physical SIM replacement. |
| What risks do eSIM hacks pose? | They can lead to account takeovers, intercepted communications, financial fraud, and service lockout. |
| How can users stay protected? | Enable strong authentication, be cautious with personal info, and monitor for unusual activity. |
| What actions should carriers take? | Secure the provisioning process, monitor for suspicious patterns, and educate users about risks. |
Conclusion
While eSIM technology enhances user convenience, it also introduces new security vulnerabilities. The latest exploit highlights how attackers are leveraging weaknesses in digital provisioning systems. To counter this, both users and mobile carriers must adopt strong security practices, continuous monitoring, and multi-factor protections to safeguard digital identities against cloning and hijacking.
Additional Resources
- GSMA: eSIM Security Guidelines
- OWASP: Mobile Security Testing Guide
- CERT: Advisories on eSIM-Related Threats
Stay informed, stay secure, protect your identity in the age of eSIM.










