What’s the Threat?
A new cyber threat is making waves: attackers are hijacking old or inactive Discord invite links to lure users into malicious servers. Once inside, victims are tricked into running dangerous scripts disguised as verification steps. These scripts silently install malware designed to steal your crypto wallet credentials, browser data, and even your Discord account.

Why Attack Discord Invite Links?
Discord invite links are usually either:
- Temporary – expire after a set time
- Permanent – never expire
- Vanity URLs – custom links (e.g., discord.gg/coolserver)
Attackers are taking advantage of links that were once valid but have expired or been deleted. Because Discord doesn’t always prevent old codes from being reused, hackers register them to direct unsuspecting users into fake servers that look official. If the original invite used only lowercase letters, it’s easier for hackers to hijack it.
Step-by-Step Breakdown of the Malware Campaign
- Link Hijacking: Criminals monitor social platforms for shared invite links that become inactive.
- Malicious Server Setup: They recreate a server using the same invite code.
- Fake Verification Bot: A bot named something like “Safeguard” asks users to verify their identity.
- Phishing Tactic: Users are sent to a fake Discord page or told to paste code into their clipboard.
- Command Execution: Victims are tricked into launching PowerShell and running the malicious command.
- Malware Download: Files are fetched from GitHub, Pastebin, or Bitbucket.
- System Compromise: Malware is quietly installed—tracking keystrokes, stealing wallets, and more.
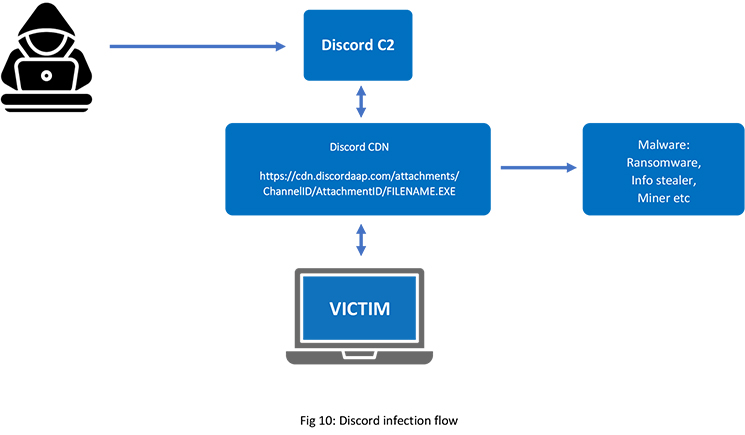
What Malware Is Being Installed?
The attack uses two main malware tools:
- AsyncRAT – Gives attackers full remote access to your system, allowing them to spy, steal files, and control your device.
- Skuld Stealer – Designed to extract saved passwords, browser autofill data, Discord tokens, and most critically, cryptocurrency wallet credentials.
These tools are delivered in layers, often using trusted platforms like GitHub and Bitbucket to hide from antivirus detection.
Who’s Being Targeted?
This malware campaign is affecting users across multiple continents:
- North America
- Europe
- Asia
Crypto investors are a major target, but anyone using Discord can fall victim—especially those joining public servers or clicking on links in forums and social media.
Recognizing Dangerous Invite Links
Some quick tips:
| Safe Practice | Risky Practice |
|---|---|
| Use permanent invites with mixed-case letters | Clicking links from old Reddit posts |
| Get links directly from a server admin | Joining servers without verifying their origin |
| Avoid vanity URLs you can’t verify | Trusting links from random social accounts |
Signs of a Fake Verification Process
A legitimate Discord bot will never ask you to:
- Open Run (
Win + R) and execute PowerShell - Paste strange clipboard content
- Install unknown software
If any of this happens, exit the server immediately and report it to Discord.
How to Stay Safe on Discord
- Enable 2FA (Two-Factor Authentication)
- Use strong, unique passwords
- Keep your antivirus software updated
- Don’t authorize bots unless you trust their source
- Never run commands you don’t understand
- Bookmark trusted server links
What To Do After an Infection
If you think you’ve been compromised:
- Disconnect your crypto wallets immediately
- Revoke access to suspicious apps via wallet settings
- Run a full malware scan with reliable antivirus
- Change all passwords, starting with email and financial accounts
- Reformat your device if you notice strange behavior or full system compromise
- Enable hardware wallets or cold storage for crypto
Frequently Asked Questions
1. Can hackers really reuse my old Discord invite?
Yes. If your server’s invite was deleted or expired, and it had only lowercase characters, it can be hijacked by attackers.
2. How are users tricked into running malware?
They’re led to believe they need to verify their identity, often with a bot asking them to run a clipboard PowerShell command.
3. What data does the malware steal?
Passwords, browser history, crypto wallet keys, Discord tokens, and potentially webcam/microphone access.
4. Is this a Discord-specific vulnerability?
Yes, it exploits how Discord reuses or allows recreation of invite URLs without properly invalidating them.
5. How can I know if an invite is safe?
Avoid links shared outside of trusted platforms. Permanent invites with uppercase letters are less likely to be hijacked.
6. What antivirus can detect this malware?
Modern, updated antivirus software (like Malwarebytes, Kaspersky, Bitdefender) can catch these tools—but only if you scan in time.
Final Thoughts & Safety Checklist
This campaign reminds us that even trusted apps like Discord can be used against us when security gaps are left unaddressed. Always stay alert, verify everything, and follow these best practices:
- ✅ Use only trusted invite links
- ✅ Double-check verification processes
- ✅ Avoid running unknown scripts or commands
- ✅ Store crypto in hardware wallets
- ✅ Monitor security news and Discord’s safety updates










