Your Ultimate Step-by-Step Guide to Become a Cybersecurity Expert
Why You Need a Cybersecurity Roadmap
Stop Guessing, Start Securing! Your Cyber Career Starts Here
The digital world is exploding. So are cyber threats. From phishing scams to ransomware attacks, the risks are real. Whether you’re a student, IT professional, or a total beginner, you need a clear, strategic cybersecurity roadmap to thrive.
This guide breaks everything down simple steps, practical tools, and expert advice, to help you build a rewarding cybersecurity career, from scratch.
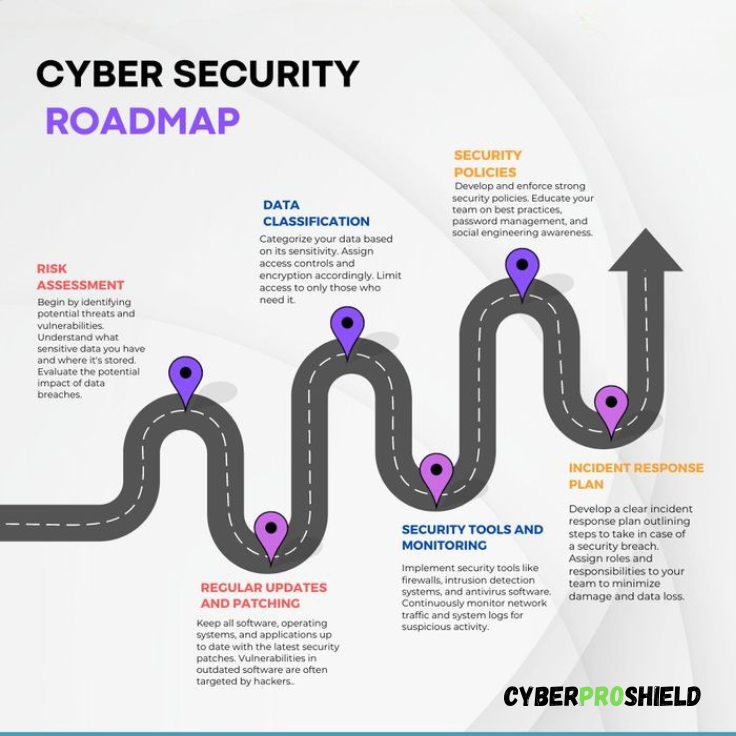
What Is a Cyber Security Route Map?
EMV Headline: “A Roadmap That Actually Works—No Fluff, Just Real Progress”
A cyber security route map is your structured plan to learn essential skills, earn certifications, and gain hands-on experience.
Step 1: Build Your Foundation
Build Your Fortress—From the Ground Up
Before hacking anything or defending networks, you need to understand how they work.
Key Areas to Cover:
- Networking Basics: TCP/IP, DNS, HTTP, ports
- Operating Systems: Windows internals, Linux commands
- Programming: Start with Python (simple + powerful)
- Security Concepts: CIA triad, encryption, access control
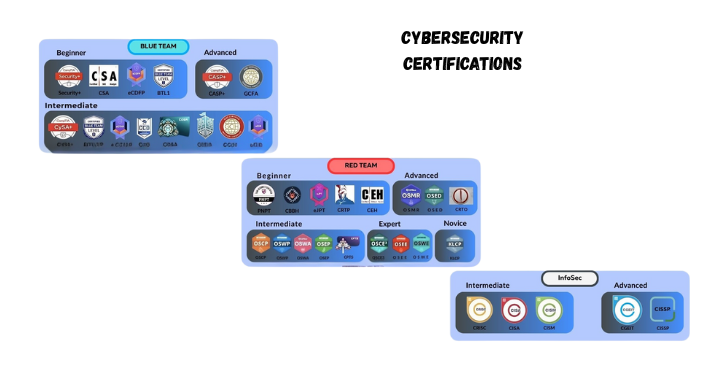
Step 2: Get Certified
Boost Credibility—Get the Right Certificates
Certifications prove your knowledge and increase job chances.
Beginner Level:
- CompTIA ITF+, Network+, Security+
Intermediate:
- CEH (Certified Ethical Hacker)
- CySA+ (Cybersecurity Analyst)
Advanced:
- OSCP (Offensive Security)
- CISSP (Security Management)
5. 🧪 Step 3: Practice in Real-World Labs
Stop Watching. Start Doing.
Theory only gets you so far. Get your hands dirty!
Practice Platforms:
- TryHackMe: Learn with guided paths
- Hack The Box: Realistic penetration tests
- CTFlearn: Capture the Flag games to sharpen skills
- Home Lab: Set up VirtualBox, Kali Linux, and test environments
Step 4: Choose Your Specialization
Find Your Role. Own Your Niche.
Cybersecurity isn’t one-size-fits-all. Here’s where you can go:
| Role | What You Do | Tools to Learn |
|---|---|---|
| SOC Analyst | Monitor & respond to threats | Splunk, SIEM |
| Penetration Tester | Ethical hacking & exploits | Kali, Burp, Metasploit |
| Cloud Security Engineer | Secure AWS/Azure/Google | Terraform, IAM, CSPM |
| Digital Forensics Expert | Investigate breaches | Autopsy, FTK, EnCase |
| GRC Consultant | Governance & compliance | ISO, NIST, GDPR |
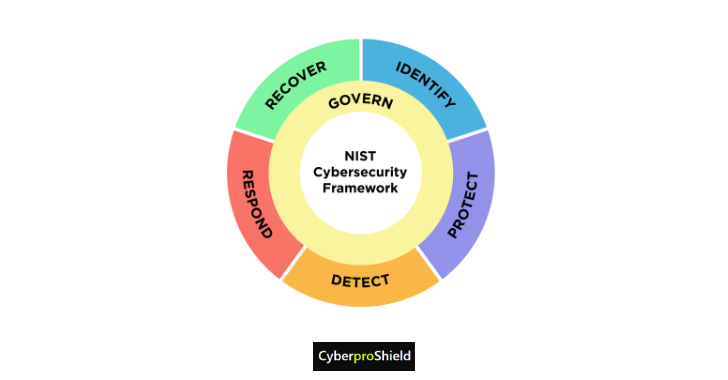
Step 5: Learn Frameworks & Security Standards
Don’t Reinvent the Wheel—Follow What Works
These frameworks help build structure and maturity in your security approach:
- NIST Cybersecurity Framework (Identify → Protect → Detect → Respond → Recover)
- CIS Controls v8 – 18 prioritized security actions
- OWASP Top 10 – Web application vulnerabilities
- Zero Trust Security Model
Step 6: Keep Up with Emerging Trends
What’s Next? Be Ready for Tomorrow’s Threats
The cyber world evolves fast. Stay ahead by learning these:
- Cloud & Container Security (Docker, Kubernetes)
- IoT Device Security (Smart homes, connected cars)
- AI/ML in Cyber Defense
- Ransomware Resilience & Recovery Plans
Step 7: Make Learning a Habit
Sharpen Your Sword Daily—Stay Informed
Cybersecurity isn’t a one-time course, it’s a lifestyle.
Stay Updated With:
- Blogs: KrebsOnSecurity, CyberSecurityNews, Dark Reading
- Feeds: CISA, US-CERT, Twitter threat hunters
- Communities: r/cybersecurity (Reddit), Discord groups, LinkedIn
- Tools: Splunk, ELK Stack, Threat Intelligence Feeds
Step 8: Apply Your Skills Professionally
Make It Count—Turn Skills Into Success
Don’t just learn—build something! Here’s how to show what you’ve got:
- Start a cybersecurity blog with writeups & guides
- Join bug bounty programs (HackerOne, Bugcrowd)
- Contribute to open-source projects on GitHub
- Apply for internships or freelance GRC/pentest gigs
Final Thoughts: Take Action Today
One Step Today, A Cyber Career Tomorrow
You don’t need to know everything to get started. Just take one step, then the next. With this roadmap, you’re no longer guessing, you’re growing.
Comment below what phase you’re in—or what you’re aiming for.
We’ll help you plan your next best move.










