In May 2025, security researchers uncovered a critical vulnerability in the NETGEAR DGND3700v2 router, identified as CVE-2025-4978. This flaw allows attackers to bypass authentication mechanisms and gain full administrative access to the router without needing valid credentials. The vulnerability is particularly concerning because it can be exploited remotely, posing significant risks to both home users and businesses relying on this router model for network connectivity.
Importance of Router Security in Modern Networks
Routers serve as the gateway between local networks and the internet, making their security paramount. A compromised router can lead to unauthorized access to connected devices, data breaches, and the potential for further network exploitation. The discovery of such a vulnerability in a widely used router model underscores the need for vigilant security practices and timely firmware updates to protect against emerging threats.
Understanding the Vulnerability
Technical Details of CVE-2025-4978
The CVE-2025-4978 vulnerability stems from an authentication bypass flaw in the router’s firmware version V1.1.00.15_1.00.15NA. The issue lies within the router’s mini_http server, which handles HTTP requests for the device’s web-based management interface. By accessing a specific endpoint, /BRS_top.html, an attacker can trigger a condition that disables the router’s authentication checks, effectively granting them unrestricted administrative access.
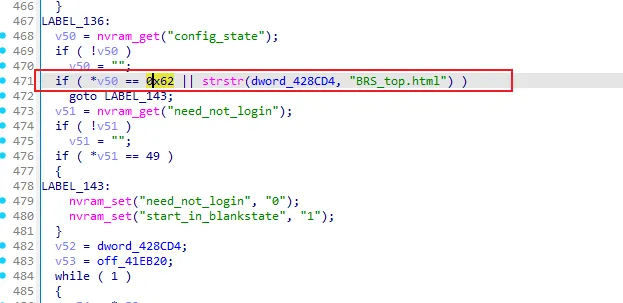
Role of the mini_http Server and BRS_top.html Endpoint
The mini_http server is a lightweight HTTP daemon responsible for managing the router’s web interface. Within this server, the function sub_406058 processes incoming HTTP requests. When the /BRS_top.html page is accessed, it sets an internal flag, start_in_blankstate, to 1. This flag alteration leads to the bypassing of HTTP Basic Authentication in the sub_404930 function, allowing attackers to access the router’s settings without authentication.
Potential Impact of the Exploit
Exploiting this vulnerability grants attackers full control over the router’s administrative functions. This access enables them to alter DNS settings, disable security features, monitor network traffic, and potentially deploy malware across connected devices. For businesses, such a breach could result in significant data loss, operational disruptions, and reputational damage.
Possible Exploitation Scenarios
Attackers could exploit this vulnerability in various ways:
- Remote Access: If remote management is enabled, attackers can exploit the flaw over the internet.
- Local Network Compromise: Gaining access to the local network through phishing or malware allows attackers to target the router directly.
- Automated Scanning: Cybercriminals may use automated tools to scan for vulnerable routers and exploit them en masse.
Affected Devices and Firmware Versions
Specific Models at Risk
The primary model affected by this vulnerability is the NETGEAR DGND3700v2. Users of this router should be particularly vigilant and take immediate action to secure their devices.
Identifying Vulnerable Firmware Versions
The vulnerability is present in firmware version V1.1.00.15_1.00.15NA. Users can check their router’s firmware version by accessing the web-based management interface and navigating to the “Firmware Version” section. If the device is running the affected firmware, it is imperative to update to the latest version promptly.
Mitigation and Recommendations
NETGEAR’s Response and Firmware Updates
Upon discovering the vulnerability, NETGEAR released a patched firmware version, V1.1.00.26, to address the issue. Users are strongly encouraged to download and install this update to secure their routers against potential exploitation.
Steps Users Should Take to Secure Their Devices
- Update Firmware: Download the latest firmware from NETGEAR’s official website and follow the provided instructions to update your router.
- Disable Remote Management: Unless necessary, disable remote management features to reduce exposure to external threats.
- Change Default Credentials: Ensure that the router’s default username and password are changed to strong, unique credentials.
- Monitor Network Activity: Regularly review connected devices and network activity for any unusual behavior.
- Stay Informed: Subscribe to security advisories from NETGEAR and other reputable sources to stay updated on potential threats.
Broader Implications for Network Security
The Importance of Regular Firmware Updates
This incident highlights the critical role of firmware updates in maintaining network security. Manufacturers often release updates to patch vulnerabilities and enhance device performance. Users should routinely check for and apply these updates to protect their networks.
Lessons Learned from the NETGEAR Vulnerability
The NETGEAR DGND3700v2 vulnerability serves as a stark reminder of the potential risks associated with outdated firmware and default configurations. It emphasizes the need for proactive security measures, including regular updates, strong authentication practices, and network monitoring, to safeguard against evolving cyber threats.
Conclusion
The discovery of the CVE-2025-4978 vulnerability in the NETGEAR DGND3700v2 router underscores the importance of robust network security practices. By understanding the nature of the threat and taking appropriate mitigation steps, users can protect their networks from unauthorized access and potential exploitation. Regular firmware updates, strong authentication measures, and vigilant monitoring are essential components of a secure network infrastructure.
FAQs
- What is CVE-2025-4978?
CVE-2025-4978 is a critical authentication bypass vulnerability in the NETGEAR DGND3700v2 router, allowing attackers to gain full administrative access without valid credentials. - How can I check if my NETGEAR router is affected?
Access your router’s web interface and check the firmware version. If it is V1.1.00.15_1.00.15NA, your device is vulnerable and requires an update. - What steps should I take if my router is vulnerable?
Immediately download and install the patched firmware version V1.1.00.26 from NETGEAR’s official website. Additionally, change default credentials and disable unnecessary remote management features. - Has NETGEAR released a fix for this vulnerability?
Yes, NETGEAR has released firmware version V1.1.00.26 to address the CVE-2025-4978 vulnerability. - How can I protect my network from similar threats in the future?
Regularly update your router’s firmware, use strong and unique passwords, disable unnecessary features, and monitor your network for unusual activity to mitigate potential threats.