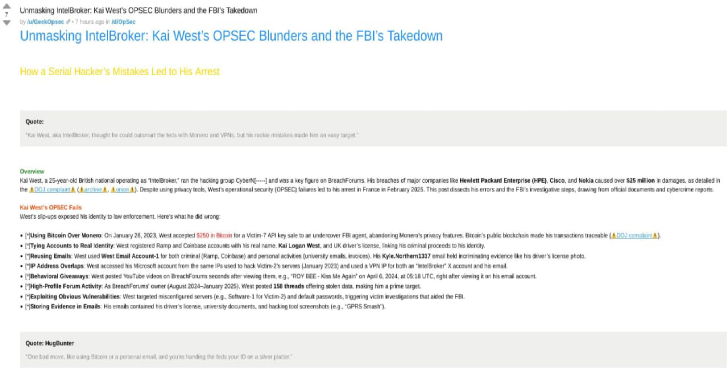
A critical zero-day vulnerability in Google Chrome has been discovered and is already being exploited by attackers in real-world scenarios. This high-severity flaw, tracked as CVE-2025-6554, impacts Chrome’s V8 JavaScript engine and gives threat actors the ability to execute arbitrary code remotely.
What Makes CVE-2025-6554 So Dangerous?
The vulnerability stems from a type confusion bug, a flaw that occurs when a program misidentifies the type of an object during execution. This confusion can corrupt memory and let attackers run malicious code directly on your device.
Even more concerning, simply visiting a compromised website could be enough to trigger this exploit. In other words, attackers don’t need to trick users into downloading anything; they just need them to land on the wrong page.
Who Discovered It?
The bug was uncovered by Clément Lecigne and Benoît Sevens from Google’s Threat Analysis Group (TAG). Their past work has exposed spyware campaigns and high-level exploits. The fact that they identified this flaw suggests it could be linked to targeted cyber-espionage efforts.
Google’s Response: Emergency Patch Rolled Out
Google responded swiftly, pushing out a security patch through Chrome’s auto-update system.
- Windows & Linux users: Secure version is 138.0.7204.96 or newer.
- macOS users: Should update to 138.0.7204.92 or later.
To manually check for updates:
- Go to your Chrome browser and type
chrome://settings/helpin the address bar. - Chrome will automatically begin checking and applying the latest version if you’re not up to date.
Chromium Browsers Also at Risk
This flaw isn’t limited to Google Chrome. Other Chromium-based browsers like:
- Microsoft Edge
- Brave
- Opera
- Vivaldi
…may also be vulnerable if updates haven’t been rolled out. Users of these browsers should check for recent patches and install updates as soon as they’re available.
Why This Matters: Exploits Already in the Wild
Google confirmed that CVE-2025-6554 is under active exploitation. That means attackers are already using it against real-world targets. This isn’t a theoretical threat, it’s happening now.
Browser vulnerabilities are highly valuable to cybercriminals because they provide direct access to users’ devices, often without any interaction. From installing spyware and keyloggers to stealing sensitive credentials, the possibilities are alarming.
How to Protect Yourself
- Update Chrome and other Chromium-based browsers immediately.
- Enable automatic updates so you never miss a security fix.
- Avoid suspicious websites and downloads.
- Use endpoint protection software that can detect malicious scripts and behavior.
If you’re part of a corporate IT team:
- Enforce browser version compliance.
- Monitor for unusual browser activity across endpoints.
- Limit access to unknown domains using DNS filtering or web proxies.
Final Thoughts: A Wake-Up Call for Web Security
CVE-2025-6554 isn’t just another Chrome bug—it’s a reminder of how fast vulnerabilities can be weaponized in the wild. The moment a zero-day is uncovered, the race begins: attackers look to exploit, while defenders rush to patch.
In today’s threat landscape, staying current is your first line of defense. Don’t wait, just update now and educate your team.