How Attackers Are Defeating Content Security Policy with Modern HTML Injection

Recent research and real-world incidents have shown that Content Security Policy (CSP), a widely used web security standard, can be bypassed by attackers using advanced HTML injection techniques. This article explains how these attacks work, highlights practical examples, and provides actionable steps to help organizations strengthen their defenses. What is Content Security Policy (CSP)? CSP is a browser feature that allows website owners to specify which sources of content (like scripts, styles, and images) are trusted. Its main goal is to prevent malicious code, such as that used in cross-site scripting (XSS) attacks, from running on web pages. While CSP is a valuable security layer, it is not immune to bypasses, especially when other vulnerabilities exist. How HTML Injection Can Bypass CSP Evolving Attack Strategies Attackers have adapted to CSP by exploiting HTML injection flaws, vulnerabilities where untrusted input is rendered as HTML. Unlike classic XSS, HTML injection does not always require JavaScript, making it a subtle but effective way to undermine CSP protections. Common Bypass Techniques Real-World Example A recent case involved a web application with a login form and dashboard protected by a nonce-based CSP. The vulnerability was due to unsanitized user input rendered via .innerHTML. Researchers combined HTML injection, CSS-based nonce leakage, and browser cache manipulation to extract the nonce and execute malicious scripts, all while CSP was active. Step-by-Step Attack Flow Impact Detection and Mitigation Detection Mitigation Expert Insights Security professionals emphasize that CSP is only one part of a robust security strategy. While it reduces the risk of XSS and code injection, attackers continue to find creative ways to bypass it. Ongoing monitoring, regular policy updates, and a layered approach are essential for effective defense. Frequently Asked Questions Question Answer (Summary) What is CSP and how does it work? CSP restricts which content sources are trusted, blocking unauthorized scripts and resources. How can attackers bypass CSP protections? Through HTML injection, nonce leakage, form hijacking, and abusing trusted endpoints. What is HTML injection and how is it different from XSS? HTML injection inserts malicious HTML, while XSS injects and executes JavaScript. Can HTML injection be used to bypass CSP? Yes, especially when combined with techniques like nonce leakage and DOM manipulation. What are real-world examples of CSP bypass techniques? Attacks using form hijacking and nonce leakage have been observed in the wild. How do you prevent HTML injection attacks? Sanitize input, use strict CSP, and avoid rendering user input as HTML. What are the limitations of CSP? CSP is not foolproof; misconfigurations and advanced attacks can bypass it. Are there payloads/tags for HTML injection on CSP-protected sites? Yes, attackers use crafted forms, CSS selectors, and DOM manipulation payloads. How do form hijacking and meta tag redirects relate to CSP bypass? They exploit HTML injection to manipulate form actions or redirect users, bypassing CSP. Conclusion Modern CSP bypass techniques using HTML injection highlight the need for continuous vigilance and layered security. Organizations must go beyond basic CSP implementation, combining strict input validation, regular policy audits, and defense-in-depth strategies to stay ahead of evolving threats. Understanding these sophisticated attack vectors and applying best practices is essential for protecting web applications and users. Table: Common CSP Bypass Techniques and Mitigations Technique Description Mitigation Strategy Form Hijacking Injecting or altering forms to steal data Sanitize input, restrict form-action DOM Manipulation Altering DOM to enable script execution Validate input, avoid dangerous patterns Nonce/Hash Leakage Extracting CSP nonces/hashes to run scripts Restrict style sources, monitor nonces Cache Exploitation Using cache to persist malicious content Control cache headers, audit CSP Trusted Endpoint Abuse Leveraging open endpoints allowed by CSP Limit trusted sources, disable JSONP
Unmasking IntelBroker: Kai West’s OPSEC Blunders & the FBI Takedown
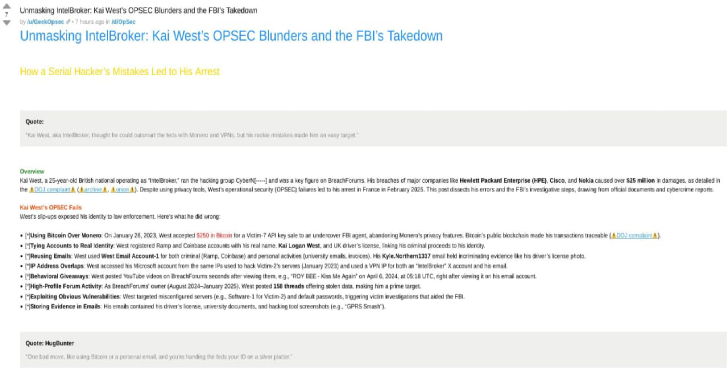
Kai West, aka IntelBroker, was exposed this week after the FBI dismantled his cybercrime empire. A 25-year-old British national, West ran a dark web operation—selling stolen data from dozens of organizations, including U.S. agencies. But authorities didn’t catch him with hi-tech surveillance—they caught him by piecing together simple mistakes. OPSEC Slip-Up #1: Same IP, Two Worlds West thought he covered his tracks, but he slipped up. Investigators matched IP logs between his BreachForums account and personal services like YouTube. Those overlapping IP addresses were the first breadcrumb leading to his real identity. OPSEC Slip-Up #2: Linking Crypto to Identity Despite preferring Monero for stealth, law enforcement traced Bitcoin transactions linked to his undercover data sales. Those payments went to wallets connected to his “Kyle Northern” email—the alias West used. This bridge cracked the case wide open. Key Findings & Charges The U.S. District Court in New York charged West with: They allege losses totaling $25 million, spanning healthcare, telecom, and government systems. West was arrested in France in February and awaits extradition. Digital Footprint That Led to Capture From 2023–2025, West sold stolen credentials, internal documents, and more on BreachForums, often under the name IntelBroker. The FBI posed as buyers, paid via cryptocurrency, and followed the money trail to an account tied to him. Combined with IP data, it became an airtight case . Why This Case Matters FAQ – Quick Answers What is IntelBroker known for?Selling data from AMD, healthcare networks, telecoms – about $25 million worth. How did the FBI find him?By tracing IP overlap and crypto payments that tied to his alias. Is he in custody?Yes—arrested in France, pending extradition to New York. Why care about an alias slip?Even small OPSEC errors can unravel large-scale cybercrime. Final Takeaway Kai West built a global hacking empire, but it all fell apart over basic digital hygiene mistakes. If you’re running a legitimate security practice, let this serve as a strong reminder: OPSEC isn’t optional.
Major Websites Hijacked: Fake Support Numbers Planted on Facebook, Netflix & Microsoft

Imagine searching for help on Facebook, Netflix, or Microsoft, and being tricked into calling a fake support number. That’s exactly what just happened. Cybercriminals have hijacked how legitimate websites display content by injecting fake phone numbers into their search results and pages. This new twist on an old scam is catching users off-guard, and it’s happening on some of the biggest platforms in the world. What Really Happened? Security researchers have uncovered a clever abuse of search parameters, those little text strings you see in a website’s URL after you run a search. For example:https://facebook.com/search?q=support What hackers realized is that many sites, including Facebook, Netflix, and Microsoft, don’t properly sanitize or validate this user input. That means if someone tweaks the URL, they can make arbitrary text, like a phone number, show up on the page. Attackers began exploiting this by inserting fraudulent customer service numbers into these search results. When unsuspecting users looked for help, they’d often see these hijacked pages in Google search results… and believe them to be legitimate. Why This Is So Dangerous Let’s say you’re having trouble with your Netflix login. You search online for “Netflix customer support,” and you click on what looks like a legit Netflix link. The page even has the official Netflix layout, logo, and branding, but there’s a fake phone number prominently listed. When you call it, you’re connected to a scammer who pretends to be a Netflix agent. They might say: These scams can lead to: Who’s Behind This? This isn’t your average script kiddie attack. These appear to be organized threat actors or SEO scammers using a technique known as Search Parameter Injection. It’s part of a broader trend where attackers manipulate how web content is rendered, without ever breaching the site itself. In many cases, attackers embed their own content (fake numbers, phishing links) into legitimate URLs. These manipulated URLs are then indexed by Google or Bing, making them look trustworthy when users search for help. And since the base domain is still “facebook.com” or “microsoft.com,” most users don’t suspect a thing. What Are Facebook, Microsoft, and Netflix Doing About It? At the time of writing, there hasn’t been a direct public statement from the affected companies. But security experts are urging these platforms to: This incident is drawing comparisons to past search parameter abuse cases, such as Google’s search redirect exploits and Apple tech support scams. How You Can Protect Yourself This kind of scam can trick even tech-savvy users. Here’s how to stay safe: The Bigger Lesson: Website Security Still Has Gaps What this shows is that even tech giants are vulnerable if input isn’t sanitized properly. Search parameter injection is a low-tech, high-impact attack that can affect any site with dynamic content. And here’s the kicker: the websites aren’t technically “hacked.” The attack happens through the front door, via poorly handled search strings and dynamic content rendering. This is a wake-up call for web developers and cybersecurity teams everywhere. You don’t need a zero-day to wreak havoc. Sometimes, a simple unchecked URL is all it takes. FAQs – What People Are Asking What is a Search Parameter Injection Attack?It’s when attackers insert text (like fake phone numbers) into a site’s search URL to make that content appear on a legitimate page. Are Facebook, Netflix, and Microsoft actually hacked?No. Their websites weren’t breached. The attackers exploited how the sites display user-generated text. Is it dangerous to call these numbers?Yes! You may be speaking to scammers trying to steal your personal or financial data. How can I verify a support number is real?Always visit the company’s official Help or Contact page—not just what you find on search engines. Final Thoughts This incident is a powerful reminder that even trusted websites can be misused in creative and malicious ways. Cybercriminals are getting more sophisticated, and they know how to manipulate search behavior, URL structures, and user trust. The best defense? Awareness, education, and vigilance. As users, we must double-check before we click or call. And as developers, it’s time to close these loopholes, because small cracks lead to big damage.
BidenCash: The Rise and Fall of a Dark Web Marketplace
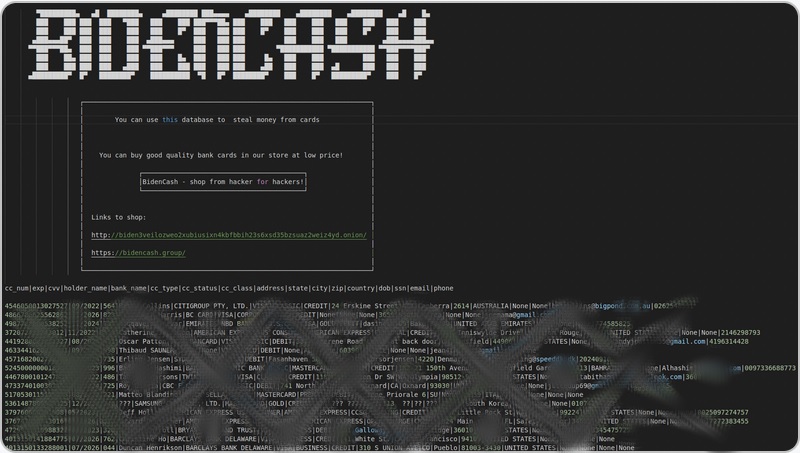
In the shadowy corners of the internet, the dark web serves as a haven for illicit activities, with marketplaces trading in everything from narcotics to stolen data. Among these, BidenCash emerged in 2022 as a notorious platform specializing in the sale of compromised credit card information and unauthorized access credentials. Its aggressive promotional tactics and expansive data dumps quickly garnered attention from cybercriminals and law enforcement alike. Origins and Operations of BidenCash Launched in June 2022, BidenCash positioned itself as a prominent player in the underground economy. The marketplace offered a user-friendly interface, allowing buyers to purchase stolen credit card details, including full card numbers, expiration dates, CVV codes, and associated personal information. Prices varied based on the perceived value of the data, with some records sold for as little as \$2. Beyond credit card information, BidenCash expanded its offerings to include SSH access credentials, providing buyers with unauthorized entry points into servers worldwide. This diversification underscored the platform’s adaptability and its operators’ intent to cater to a broad spectrum of cybercriminal needs. Data Dumps as Marketing Strategy BidenCash’s notoriety wasn’t solely due to its inventory but also its unconventional marketing strategies. To commemorate its one-year anniversary in February 2023, the platform released a data dump containing over 2 million compromised credit and debit card records on a Russian-speaking darknet forum. This wasn’t an isolated incident; subsequent dumps included: These data dumps served dual purposes: attracting new users by showcasing the platform’s vast data reserves and asserting dominance in the competitive dark web marketplace landscape. Law Enforcement Crackdown The audacity of BidenCash’s operations didn’t go unnoticed. On June 4, 2025, a coordinated international law enforcement operation led by the U.S. Secret Service and the FBI, with support from the Dutch National Police, The ShadowServer Foundation, and Searchlight Cyber, successfully seized multiple domains associated with BidenCash. Visitors to the platform’s dark web domain were met with a banner indicating the site’s seizure due to its involvement in illegal activities. This takedown marked a significant victory in the ongoing battle against cybercrime, disrupting one of the most active marketplaces trafficking in stolen financial data. Implications and the Broader Cybercrime Landscape The operations of platforms like BidenCash have profound implications: While the shutdown of BidenCash represents progress, the persistent demand for stolen data ensures that similar platforms will continue to emerge, necessitating ongoing vigilance and international cooperation in cybersecurity efforts. Conclusion BidenCash’s trajectory from its inception to its eventual dismantling highlights the dynamic and resilient nature of cybercriminal enterprises. As technology evolves, so too do the methods employed by threat actors. Combating such threats requires a multifaceted approach, combining technological defenses, public awareness, and robust international law enforcement collaboration. Frequently Asked Questions Q1: What was BidenCash?A1: BidenCash was a dark web marketplace launched in 2022, specializing in the sale of stolen credit card information and unauthorized access credentials. Q2: How did BidenCash attract users?A2: The platform released large datasets of compromised financial information for free, serving as a promotional tactic to showcase its inventory and attract cybercriminal clientele. Q3: What led to the shutdown of BidenCash?A3: A coordinated international law enforcement operation, involving agencies like the U.S. Secret Service and the FBI, seized multiple domains associated with BidenCash in June 2025. Q4: What risks did BidenCash pose to individuals?A4: By facilitating the sale of stolen financial data, BidenCash increased the risk of identity theft, unauthorized transactions, and broader cyberattacks targeting individuals and organizations. Q5: How can individuals protect themselves from such threats?A5: Regularly monitoring financial statements, using strong and unique passwords, enabling two-factor authentication, and staying informed about data breaches can help mitigate risks associated with stolen data marketplaces.
Mirai IoT Botnet
Understanding the Mirai IoT Botnet Introduction to IoT Botnets The Internet of Things (IoT) has revolutionized the way we interact with technology, connecting everyday devices like cameras, thermostats, and refrigerators to the internet. While this connectivity offers convenience, it also introduces significant security vulnerabilities. One of the most notorious examples of exploiting these vulnerabilities is the Mirai botnet, which harnessed the power of compromised IoT devices to launch massive cyberattacks. What is an IoT Botnet? An IoT botnet is a network of internet-connected devices infected with malicious software and controlled as a group without the owners’ knowledge. These devices, often with minimal security measures, can be co-opted to perform coordinated tasks such as Distributed Denial of Service (DDoS) attacks, data theft, or spam distribution. The Mirai botnet exemplifies the potential scale and impact of such networks. The Rise of IoT Devices and Security Gaps The proliferation of IoT devices has outpaced the implementation of robust security protocols. Many devices are shipped with default usernames and passwords, which users often neglect to change. Additionally, manufacturers may not provide regular software updates, leaving devices vulnerable to known exploits. These security gaps create an environment ripe for exploitation by malware like Mirai. Origins of the Mirai Botnet The Mirai botnet emerged in 2016, developed by three college students: Paras Jha, Josiah White, and Dalton Norman. Initially intended to gain an advantage in the Minecraft gaming community by overwhelming competitors’ servers, Mirai quickly evolved into a tool capable of launching unprecedented DDoS attacks. The creators released the source code publicly, leading to widespread adoption and adaptation by other malicious actors. Timeline of Mirai’s Initial Attacks These attacks highlighted the vulnerabilities inherent in IoT devices and the potential for widespread disruption. How the Mirai Botnet Works Mirai operates by scanning the internet for IoT devices with open Telnet ports (23 and 2323) and attempting to log in using a list of common default credentials. Once access is gained, the malware infects the device, turning it into a “bot” that can receive commands from a central server. The botnet can then be directed to launch DDoS attacks, overwhelming targeted servers with traffic. Default Credentials Exploitation A critical factor in Mirai’s success was its exploitation of default credentials. Many IoT devices are shipped with factory-set usernames and passwords, such as “admin/admin” or “user/1234,” which users often fail to change. Mirai’s hardcoded list of over 60 such credentials allowed it to rapidly compromise a vast number of devices. Command and Control (C&C) Infrastructure Infected devices communicate with a Command and Control (C&C) server, which issues instructions for scanning, infection, and launching attacks. This centralized control structure enables coordinated actions across the botnet. Some variants of Mirai have adopted decentralized models to evade detection and takedown efforts. Major Attacks Launched by Mirai Technical Anatomy of Mirai Mirai’s codebase is relatively simple and modular, written in C for the bot and Go for the controller. Its lightweight design allows it to run on devices with limited processing power. The malware includes components for scanning, brute-force login attempts, and executing various types of DDoS attacks, such as TCP, UDP, and HTTP floods. Propagation Techniques Mirai spreads by continuously scanning IP ranges for devices with open Telnet ports. Upon finding a target, it attempts to log in using its list of default credentials. Successful logins result in the device being infected and added to the botnet. The malware also removes competing malware and disables remote administration to maintain control over the device. Botnet Lifecycle Management The lifecycle of a Mirai-infected device includes: Variants and Evolution of Mirai Since the release of its source code, numerous Mirai variants have emerged, each with unique features: These variants demonstrate the adaptability of Mirai’s code and the ongoing threat it poses. Global Impact and Case Studies These incidents underscore the botnet’s capacity to affect various sectors and geographies. Legal Consequences and Creator Sentencing The creators of Mirai were apprehended and pled guilty to charges related to computer fraud. As part of their sentencing, they cooperated with the FBI, assisting in cybersecurity efforts and contributing to the development of tools to combat similar threats. Their case highlights the potential for rehabilitation and the importance of leveraging technical expertise in cybersecurity defense. Mitigation Strategies and Best Practices To protect against threats like Mirai: Implementing these measures can significantly reduce the risk of infection. The Ongoing Threat of IoT Botnets Despite increased awareness, many IoT devices remain vulnerable due to poor security practices. As the number of connected devices grows, so does the potential for exploitation. Continuous vigilance, user education, and industry-wide standards are essential to mitigate the risks posed by botnets like Mirai. Conclusion The Mirai botnet serves as a stark reminder of the vulnerabilities inherent in the rapidly expanding IoT landscape. Its ability to compromise vast numbers of devices and launch large-scale attacks underscores the need for robust security measures. By understanding the mechanisms of such threats and implementing proactive defenses, individuals and organizations can better protect themselves in an increasingly connected world. FAQs Q1: How can I tell if my IoT device is infected with Mirai? A1: Signs include sluggish device performance, unexpected reboots, or unusual network traffic. Monitoring tools can help detect anomalies. Q2: Does rebooting my device remove Mirai? A2: Yes, Mirai resides in volatile memory and is removed upon reboot. However, if default credentials remain unchanged, the device can be reinfected quickly. Q3: Are all IoT devices vulnerable to Mirai? A3: Devices with default or weak credentials and open Telnet ports are particularly at risk. Regular updates and strong passwords enhance security. Q4: Can antivirus software protect against Mirai? A4: Traditional antivirus solutions may not be effective on IoT devices. Network-level security measures and proper device configuration are more effective. Q5: What should manufacturers do to prevent such botnets? A5: Manufacturers should enforce secure default settings, provide regular firmware updates, and educate users on best security practices.
Critical NETGEAR Router Vulnerability Let Attackers Gain Full Admin Access
In May 2025, security researchers uncovered a critical vulnerability in the NETGEAR DGND3700v2 router, identified as CVE-2025-4978. This flaw allows attackers to bypass authentication mechanisms and gain full administrative access to the router without needing valid credentials. The vulnerability is particularly concerning because it can be exploited remotely, posing significant risks to both home users and businesses relying on this router model for network connectivity. Importance of Router Security in Modern Networks Routers serve as the gateway between local networks and the internet, making their security paramount. A compromised router can lead to unauthorized access to connected devices, data breaches, and the potential for further network exploitation. The discovery of such a vulnerability in a widely used router model underscores the need for vigilant security practices and timely firmware updates to protect against emerging threats. Understanding the Vulnerability Technical Details of CVE-2025-4978 The CVE-2025-4978 vulnerability stems from an authentication bypass flaw in the router’s firmware version V1.1.00.15_1.00.15NA. The issue lies within the router’s mini_http server, which handles HTTP requests for the device’s web-based management interface. By accessing a specific endpoint, /BRS_top.html, an attacker can trigger a condition that disables the router’s authentication checks, effectively granting them unrestricted administrative access. Role of the mini_http Server and BRS_top.html Endpoint The mini_http server is a lightweight HTTP daemon responsible for managing the router’s web interface. Within this server, the function sub_406058 processes incoming HTTP requests. When the /BRS_top.html page is accessed, it sets an internal flag, start_in_blankstate, to 1. This flag alteration leads to the bypassing of HTTP Basic Authentication in the sub_404930 function, allowing attackers to access the router’s settings without authentication. Potential Impact of the Exploit Exploiting this vulnerability grants attackers full control over the router’s administrative functions. This access enables them to alter DNS settings, disable security features, monitor network traffic, and potentially deploy malware across connected devices. For businesses, such a breach could result in significant data loss, operational disruptions, and reputational damage. Possible Exploitation Scenarios Attackers could exploit this vulnerability in various ways: Affected Devices and Firmware Versions Specific Models at Risk The primary model affected by this vulnerability is the NETGEAR DGND3700v2. Users of this router should be particularly vigilant and take immediate action to secure their devices. Identifying Vulnerable Firmware Versions The vulnerability is present in firmware version V1.1.00.15_1.00.15NA. Users can check their router’s firmware version by accessing the web-based management interface and navigating to the “Firmware Version” section. If the device is running the affected firmware, it is imperative to update to the latest version promptly. Mitigation and Recommendations NETGEAR’s Response and Firmware Updates Upon discovering the vulnerability, NETGEAR released a patched firmware version, V1.1.00.26, to address the issue. Users are strongly encouraged to download and install this update to secure their routers against potential exploitation. Steps Users Should Take to Secure Their Devices Broader Implications for Network Security The Importance of Regular Firmware Updates This incident highlights the critical role of firmware updates in maintaining network security. Manufacturers often release updates to patch vulnerabilities and enhance device performance. Users should routinely check for and apply these updates to protect their networks. Lessons Learned from the NETGEAR Vulnerability The NETGEAR DGND3700v2 vulnerability serves as a stark reminder of the potential risks associated with outdated firmware and default configurations. It emphasizes the need for proactive security measures, including regular updates, strong authentication practices, and network monitoring, to safeguard against evolving cyber threats. Conclusion The discovery of the CVE-2025-4978 vulnerability in the NETGEAR DGND3700v2 router underscores the importance of robust network security practices. By understanding the nature of the threat and taking appropriate mitigation steps, users can protect their networks from unauthorized access and potential exploitation. Regular firmware updates, strong authentication measures, and vigilant monitoring are essential components of a secure network infrastructure. FAQs