
A newly disclosed vulnerability in ModSecurity, one of the most widely adopted Web Application Firewalls (WAFs), has raised alarms in...
Explore our blog to discover industry insights, and the latest trends.

A newly disclosed vulnerability in ModSecurity, one of the most widely adopted Web Application Firewalls (WAFs), has raised alarms in...

A critical zero-day vulnerability in Google Chrome has been discovered and is already being exploited by attackers in real-world scenarios....

Zig Strike isn’t just another payload generator, it’s a full-on offensive toolkit built in the Zig programming language, purpose‑made to...
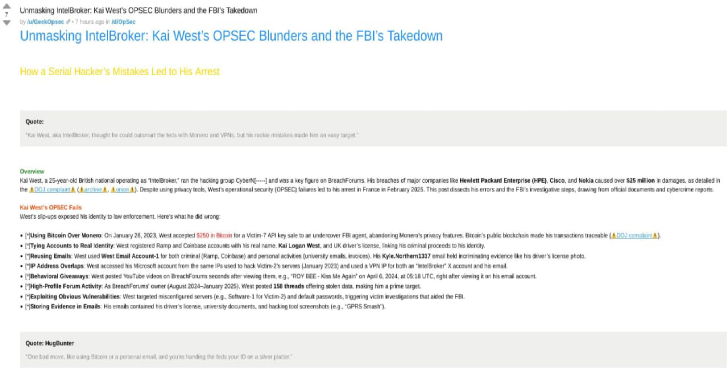
Kai West, aka IntelBroker, was exposed this week after the FBI dismantled his cybercrime empire. A 25-year-old British national, West...

The U.S. House of Representatives has officially banned the use of WhatsApp on all House-managed devices. Staff members are being...

Imagine searching for help on Facebook, Netflix, or Microsoft, and being tricked into calling a fake support number. That’s exactly...

What Is a DoS Attack, Really? Let’s break it down simply: A Denial of Service (DoS) attack is like jamming...

Your Ultimate Step-by-Step Guide to Become a Cybersecurity Expert Why You Need a Cybersecurity Roadmap Stop Guessing, Start Securing! Your...

How These Hidden Flaws Could Hand Over Your Entire System to Hackers 1. The Silent Power Grab Happening Inside Your...

What is Apache Tomcat? Apache Tomcat is an open-source web server and servlet container widely used to deploy Java-based web...

In the ever-evolving realm of software supply chain security, malicious packages are becoming stealthier, more strategic, and more damaging. Recently,...

Kali Linux 2025.2 marks a major milestone in penetration testing distributions, introducing advanced features like smartwatch Wi-Fi injection, an Android...

What’s the Threat? A new cyber threat is making waves: attackers are hijacking old or inactive Discord invite links to...

Why iOS Is a High-Value Target Apple’s iOS is often praised for its security, but that very reputation makes it...

Cybersecurity in Today’s Digital Age In this digital era, in which the world has become a global village, protecting digital...

Cybercriminal activity targeting American users has surged, prompting a stark warning from Google’s Threat Analysis Group (TAG). According to a...

On this month’s Patch Tuesday, Microsoft unveiled the Windows 11 cumulative update KB5060842, a pivotal release packed with essential fixes,...

In the digital labyrinth of likes, follows, and hashtags, many Instagram users fall prey to the glittering illusion of rapid...

In the ever-evolving landscape of digital security, reactive defense is no longer enough. Modern adversaries don’t knock they slip through...

In a world where cyber threats are growing more sophisticated by the day, a dangerous malware strain known as Bitter...

In a shocking revelation that once again highlights the ongoing cyberwar between global tech powers, a new cybersecurity report has...