Recent research and real-world incidents have shown that Content Security Policy (CSP), a widely used web security standard, can be bypassed by attackers using advanced HTML injection techniques. This article explains how these attacks work, highlights practical examples, and provides actionable steps to help organizations strengthen their defenses.
What is Content Security Policy (CSP)?
CSP is a browser feature that allows website owners to specify which sources of content (like scripts, styles, and images) are trusted. Its main goal is to prevent malicious code, such as that used in cross-site scripting (XSS) attacks, from running on web pages. While CSP is a valuable security layer, it is not immune to bypasses, especially when other vulnerabilities exist.
How HTML Injection Can Bypass CSP
Evolving Attack Strategies
Attackers have adapted to CSP by exploiting HTML injection flaws, vulnerabilities where untrusted input is rendered as HTML. Unlike classic XSS, HTML injection does not always require JavaScript, making it a subtle but effective way to undermine CSP protections.
Common Bypass Techniques
- Form Hijacking: Injecting or modifying forms to redirect user data to attacker-controlled servers. This can be done by changing the
formactionattribute or adding new forms. Password managers may autofill credentials into these forms, increasing the risk of theft. - DOM Manipulation: Injected HTML elements can alter the Document Object Model (DOM), sometimes enabling script execution or data exfiltration even with CSP in place.
- Nonce and Hash Leakage: Attackers may use CSS or other methods to leak CSP nonces or hashes, which are intended to allow only trusted scripts. With these, they can execute unauthorized code.
- Cache Exploitation: Manipulating browser cache can allow malicious content to persist, even when nonce-based CSP is used.
- Trusted Endpoint Abuse: If a CSP policy allows scripts from certain domains (such as open JSONP endpoints), attackers may exploit these to run malicious code.
Real-World Example
A recent case involved a web application with a login form and dashboard protected by a nonce-based CSP. The vulnerability was due to unsanitized user input rendered via .innerHTML. Researchers combined HTML injection, CSS-based nonce leakage, and browser cache manipulation to extract the nonce and execute malicious scripts, all while CSP was active.
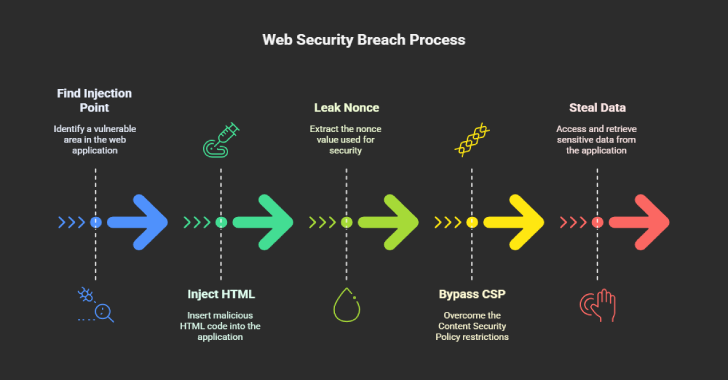
Step-by-Step Attack Flow
- Find an Injection Point: The attacker locates a field where user input is rendered as HTML without proper sanitization.
- Inject Malicious HTML: The attacker adds a form or manipulates attributes to redirect data.
- Leak Nonce or Hash (if present): Through CSS or other means, the attacker extracts the nonce or hash value.
- Bypass CSP: With the nonce or hash, the attacker injects a script or payload that passes CSP checks.
- Steal Data: The attacker collects credentials or sensitive information via the compromised form or script.
Impact
- Credential Theft: Stolen usernames and passwords, especially when password managers autofill into injected forms.
- Session Hijacking: Unauthorized access to user accounts or sensitive data.
- Persistent Threats: Cache manipulation and nonce leakage can allow attacks to persist across sessions.
- Reputation Damage: Successful attacks can erode user trust and harm organizational reputation.
Detection and Mitigation
Detection
- Monitor for unexpected form submissions and new forms in the DOM.
- Enable and review CSP violation reports to spot bypass attempts.
- Log suspicious HTML or CSS in user-generated content.
Mitigation
- Sanitize User Input: Always validate and sanitize input before rendering it as HTML.
- Enforce Strict CSP: Use nonce- or hash-based CSPs, avoid
unsafe-inline, and restrict allowed sources as much as possible. - Configure
form-actionDirective: Specify allowed form destinations to prevent data exfiltration. - Remove Unnecessary Features: Disable or restrict features like JSONP endpoints and inline event handlers.
- Audit CSP Policies Regularly: Test for misconfigurations and update policies to address new threats.
- Layered Security: Combine CSP with input validation, output encoding, and secure development practices.
Expert Insights
Security professionals emphasize that CSP is only one part of a robust security strategy. While it reduces the risk of XSS and code injection, attackers continue to find creative ways to bypass it. Ongoing monitoring, regular policy updates, and a layered approach are essential for effective defense.
Frequently Asked Questions
| Question | Answer (Summary) |
|---|---|
| What is CSP and how does it work? | CSP restricts which content sources are trusted, blocking unauthorized scripts and resources. |
| How can attackers bypass CSP protections? | Through HTML injection, nonce leakage, form hijacking, and abusing trusted endpoints. |
| What is HTML injection and how is it different from XSS? | HTML injection inserts malicious HTML, while XSS injects and executes JavaScript. |
| Can HTML injection be used to bypass CSP? | Yes, especially when combined with techniques like nonce leakage and DOM manipulation. |
| What are real-world examples of CSP bypass techniques? | Attacks using form hijacking and nonce leakage have been observed in the wild. |
| How do you prevent HTML injection attacks? | Sanitize input, use strict CSP, and avoid rendering user input as HTML. |
| What are the limitations of CSP? | CSP is not foolproof; misconfigurations and advanced attacks can bypass it. |
| Are there payloads/tags for HTML injection on CSP-protected sites? | Yes, attackers use crafted forms, CSS selectors, and DOM manipulation payloads. |
| How do form hijacking and meta tag redirects relate to CSP bypass? | They exploit HTML injection to manipulate form actions or redirect users, bypassing CSP. |
Conclusion
Modern CSP bypass techniques using HTML injection highlight the need for continuous vigilance and layered security. Organizations must go beyond basic CSP implementation, combining strict input validation, regular policy audits, and defense-in-depth strategies to stay ahead of evolving threats. Understanding these sophisticated attack vectors and applying best practices is essential for protecting web applications and users.
Table: Common CSP Bypass Techniques and Mitigations
| Technique | Description | Mitigation Strategy |
|---|---|---|
| Form Hijacking | Injecting or altering forms to steal data | Sanitize input, restrict form-action |
| DOM Manipulation | Altering DOM to enable script execution | Validate input, avoid dangerous patterns |
| Nonce/Hash Leakage | Extracting CSP nonces/hashes to run scripts | Restrict style sources, monitor nonces |
| Cache Exploitation | Using cache to persist malicious content | Control cache headers, audit CSP |
| Trusted Endpoint Abuse | Leveraging open endpoints allowed by CSP | Limit trusted sources, disable JSONP |