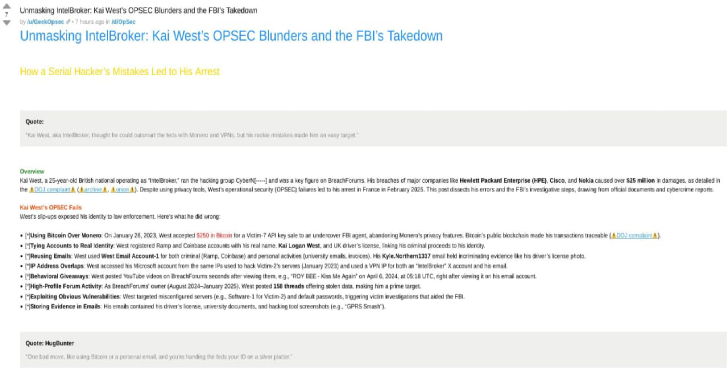
Kai West, aka IntelBroker, was exposed this week after the FBI dismantled his cybercrime empire. A 25-year-old British national, West ran a dark web operation—selling stolen data from dozens of organizations, including U.S. agencies. But authorities didn’t catch him with hi-tech surveillance—they caught him by piecing together simple mistakes.
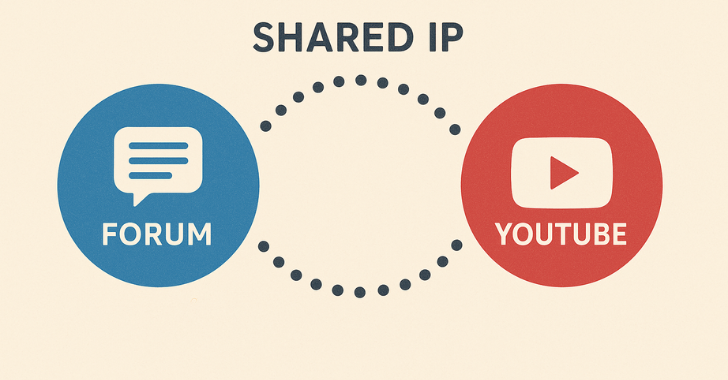
OPSEC Slip-Up #1: Same IP, Two Worlds
West thought he covered his tracks, but he slipped up. Investigators matched IP logs between his BreachForums account and personal services like YouTube. Those overlapping IP addresses were the first breadcrumb leading to his real identity.
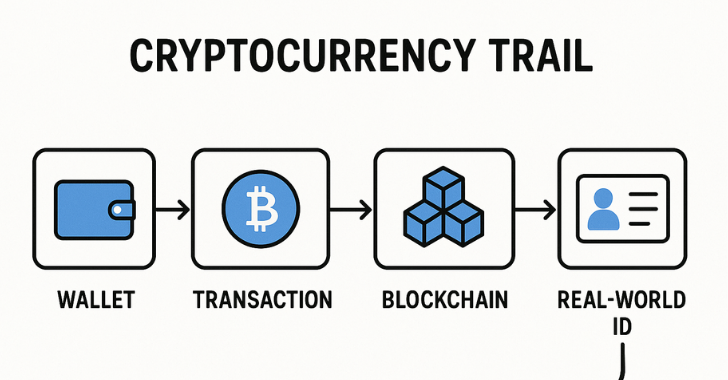
OPSEC Slip-Up #2: Linking Crypto to Identity
Despite preferring Monero for stealth, law enforcement traced Bitcoin transactions linked to his undercover data sales. Those payments went to wallets connected to his “Kyle Northern” email—the alias West used. This bridge cracked the case wide open.
Key Findings & Charges
The U.S. District Court in New York charged West with:
- Computer intrusion
- Wire fraud
- Unauthorized data access
They allege losses totaling $25 million, spanning healthcare, telecom, and government systems. West was arrested in France in February and awaits extradition.
Digital Footprint That Led to Capture
From 2023–2025, West sold stolen credentials, internal documents, and more on BreachForums, often under the name IntelBroker. The FBI posed as buyers, paid via cryptocurrency, and followed the money trail to an account tied to him. Combined with IP data, it became an airtight case .
Why This Case Matters
- Proof that OPSEC is everything. One shared IP or linked payment can undo years of cybercrime.
- Global law enforcement cooperation worked. FBI, French, and UK agencies combined forces.
- Clear message for cybercriminals. Even sophisticated hackers are only as secure as their weakest connection.
FAQ – Quick Answers
What is IntelBroker known for?
Selling data from AMD, healthcare networks, telecoms – about $25 million worth.
How did the FBI find him?
By tracing IP overlap and crypto payments that tied to his alias.
Is he in custody?
Yes—arrested in France, pending extradition to New York.
Why care about an alias slip?
Even small OPSEC errors can unravel large-scale cybercrime.
Final Takeaway
Kai West built a global hacking empire, but it all fell apart over basic digital hygiene mistakes. If you’re running a legitimate security practice, let this serve as a strong reminder: OPSEC isn’t optional.