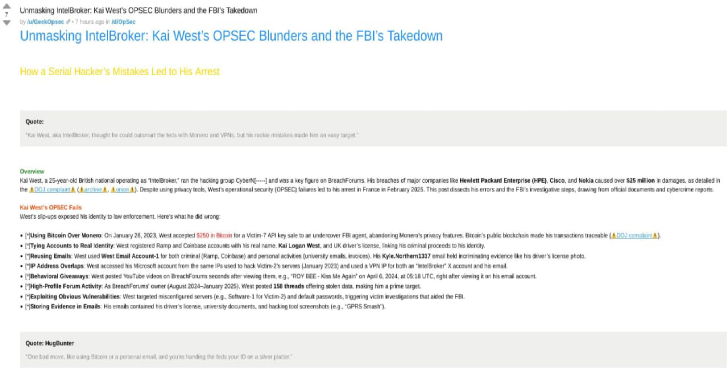
What Is a DoS Attack, Really?
Let’s break it down simply: A Denial of Service (DoS) attack is like jamming the phone lines of a business so real customers can’t get through.
Instead of phone calls, it floods a website or online service with so much fake traffic that it slows down, or completely crashes. The goal? To make sure the service becomes unavailable to real users.
How Does a DoS Attack Work?
DoS attacks overwhelm resources like bandwidth, memory, or CPU usage.
Here’s a basic example:
- A hacker sends thousands (or millions) of requests to a website.
- The server can’t handle it all.
- The website becomes super slow or stops responding entirely.
Think of it like pouring water into a glass non-stop until it spills.
Types of DoS Attacks
DoS isn’t one-size-fits-all. Some common types include:
- Volumetric Attacks – Flooding bandwidth with traffic (e.g., UDP floods).
- Protocol Attacks – Exploiting server weaknesses (e.g., SYN floods).
- Application Layer Attacks – Targeting specific apps/services (e.g., HTTP floods).
Each type hits a different layer of the network stack, but the goal is always the same: make the service go dark.
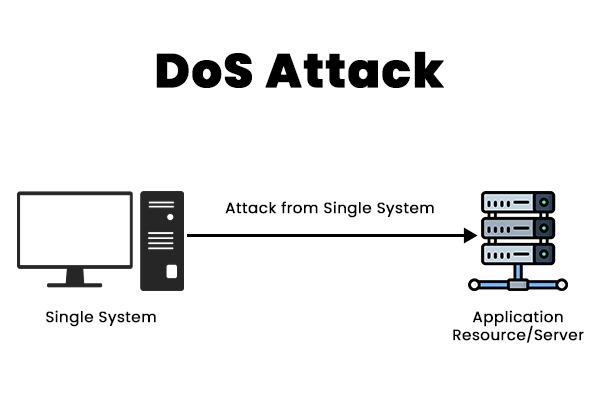
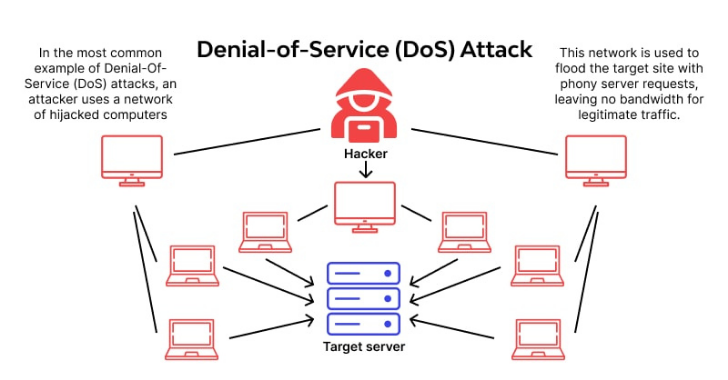
DDoS vs. DoS – What’s the Difference?
DoS is a single source attack.
DDoS (Distributed Denial of Service)? That’s when an army of infected devices (aka a botnet) attack all at once.
Imagine one person yelling at a receptionist non-stop (DoS) vs. an entire crowd doing it (DDoS). The impact is much worse.
Why Do Attackers Launch DoS Attacks?
Motivations vary, but common reasons include:
- Revenge or protest (hacktivism)
- Ransom attacks (“Pay or we’ll keep attacking”)
- Business rivalry sabotage
- Testing security vulnerabilities
Sometimes, it’s even just for fun—yes, some hackers are just showing off.
Real-Life DoS Attack Examples
Example 1: GitHub – The Largest DDoS Ever
In 2018, GitHub was slammed with 1.35 Tbps of traffic—one of the biggest attacks in history. Luckily, they recovered quickly using automated mitigation tools.
Example 2: Dyn DNS Attack
In 2016, major websites like Twitter, Netflix, and Reddit went down due to a DDoS attack on Dyn, a key DNS provider.
How Can You Protect Against DoS Attacks?
Here are practical defenses:
- Rate limiting – Restrict traffic from the same IP.
- Web Application Firewalls (WAFs) – Block malicious requests.
- Cloud-based DDoS Protection – Use services like Cloudflare, AWS Shield.
- Redundancy – Distribute services across multiple servers/regions.
Prevention isn’t perfect, but mitigation can make a huge difference.
Final Thoughts – Why This Matters to Everyone
You don’t need to run a huge tech company to be affected. Small businesses, e-commerce stores, schools—anyone online is a potential target.
With DoS attacks becoming more affordable (even rentable via the dark web), it’s vital to stay informed and protected.
Knowing the basics could save you hours of downtime and thousands of dollars.

FAQs: Quick Answers to Popular Questions
What is the difference between DoS and DDoS?
A DoS comes from one source; a DDoS comes from many (usually a botnet).
Can DoS attacks be traced?
Yes, but it’s challenging if attackers use spoofed IPs or VPNs.
Are DoS attacks illegal?
Absolutely. Launching a DoS attack is a criminal offense in most countries, including the U.S.
How long do DoS attacks last?
They can last from minutes to hours or even days, depending on the attacker’s goal and defenses in place.
Can my website be a target?
Yes. Any online service can be a target—especially if it handles transactions, stores user data, or has competitors.










1 Comment
[…] […]
Your comment is awaiting moderation.
9eftla