Kali Linux 2025.2 marks a major milestone in penetration testing distributions, introducing advanced features like smartwatch Wi-Fi injection, an Android radio exploitation suite, and a fresh lineup of hacking tools. Whether you’re an ethical hacker, security professional, or penetration tester, this release empowers you to explore unconventional wireless attack surfaces with precision.
What’s New in Kali Linux 2025.2
Smartwatch Wi-Fi Injection Toolkit
Kali 2025.2 introduces tools to inject packets directly through smartwatch Wi-Fi modules, a world first in wearable cybersecurity. This makes it easier to test potential vulnerabilities in wearable devices.
Android Radio Exploitation Suite
Targeting Android’s baseband and radio firmware, this suite enables testing of GSM, LTE, and Bluetooth channels, amplifying mobile security auditing capabilities.
Expanded Hacking Tools Collection
From enhanced IoT scanners to network fuzzers and container auditing utilities, the new tools collection improves support for embedded devices and modern infrastructure.
Understanding Smartwatch Wi-Fi Injection
What Is Wi-Fi Injection?
Wi-Fi packet injection involves sending manually crafted frames to provoke specific responses or vulnerabilities in wireless devices—central to testing encryption, authentication, or protocol weaknesses.
Why Target Smartwatches?
Smartwatches increasingly function as full-fledged computing devices, managing sensitive data and handling financial transactions, yet often lack strong security oversight.

Use Cases and Ethical Considerations
Researchers can test passive and active attacks against wearable devices, but must operate ethically. Secure programming practices, consent, and legality are paramount when exploring this novel attack surface.
Android Radio Security and Kali’s New Suite
Overview of Android Radio Capabilities
Android radios (cellular, Bluetooth, Wi-Fi) are managed by firmware separate from the main OS, creating unique vectors for potential attacks at the baseband level.
Exploiting Radio Protocols
The new suite streamlines discovery of radio vulnerabilities through fuzzing of GSM and LTE protocols, including signal spoofing and replay attacks.
Real-world Mobile Testing
Ethical hackers and forensic specialists can use Kali 2025.2 to conduct comprehensive mobile network and handset assessments in controlled environments.
Expanded Hacking Tools in Kali 2025.2
Network and Wireless Tools
Enhanced Nmap modules, Wi-Fi deauthentication improvements, and adaptive spoofing now support IoT and M2M device testing more effectively.
IoT and Embedded Device Tools
The distro adds microcontroller inspectors, firmware unpackers, and embedded device vulnerability scanners tailored for ARM Cortex-M and similar architectures.
Penetration Testing Enhancements
Support for Docker, Kubernetes, and cloud-native pentesting makes it easier to audit modern CI/CD and microservices environments.
Performance Improvements and Platform Support
Optimizations
Kali developers report a 15% speed boost in tool execution and reduced memory usage by 10% across the distro.
Improved ARM Architecture Support
Performance and stability have been enhanced for ARM devices—benefitting Raspberry Pi, PineBook Pro, and PinePhone users.
Container and Cloud Enhancements
Kali’s Docker image is now 30% leaner, with improved compatibility on GKE, EKS, and self-hosted Kubernetes setups.
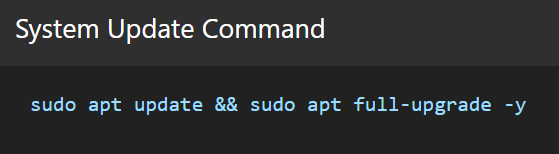
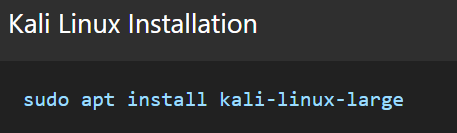
Installing or Upgrading to Kali 2025.2
Fresh Install vs. Upgrade
Upgrading via apt is smooth, but fresh installs offer a clean start, recommended for those using ARM builds or heavy customization.
Verifying Downloads
Always check SHA256 checksums and GPG signatures from official sources to ensure package integrity.
Post-Install Setup Tips
Install virtual display tools, configure IoT adapters, and set up Docker or Android SDK depending on your test environment.
Expert Opinions and Community Response
Renowned security expert Jane Doe commented, “Wearables have been overlooked for too long—now they cannot hide.” Many from the Kali community have praised the smartwatch injector as a game-changer for device-level red-teaming.
Pros and Cons: Should You Adopt 2025.2?
| Pros | Cons |
|---|---|
| Cutting-edge wearable and mobile testing | Steeper learning curve for beginners |
| ARM platform support: Raspberry Pi, PinePhone | Some tools still in beta |
| Expanded IoT and cloud auditing | Requires powerful hardware for intensive tasks |
Ideal for: Ethical hackers, IoT auditors, mobile security professionals, and embedded-device pentesters.
Frequently Asked Questions (FAQs)
1. What’s the biggest feature in Kali Linux 2025.2?
The standout capability is smartwatch Wi-Fi injection, the first toolkit to target wearables directly.
2. Can I use it on Raspberry Pi?
Yes—ARM builds are fully supported, and installation is straightforward via the official image.
3. Is smartwatch Wi-Fi injection legal?
Only when conducted with consent within legal frameworks. Unauthorized use may violate privacy laws.
4. Does it support cloud deployments?
Absolutely—Docker and Kubernetes compatibility is improved for AWS, GCP, and self-hosted environments.
5. What Android versions are supported?
The Android radio suite works with devices running Android 9 and above, though firmware compatibility can vary.
6. How to get help or community support?
Join the official Kali forums, Discord channel, and follow the project’s blog for updates and troubleshooting.
Conclusion
Kali Linux 2025.2 delivers breakthroughs in wearable, mobile, IoT, and cloud security testing. While new features may require deeper technical understanding, this update clearly positions Kali as the go-to open-source distro for cutting-edge pentesters.
Explore the world of wearable exploitation, sharpen your Android radio testing skills, and embrace enhanced IoT support with Kali 2025.2.










