Why iOS Is a High-Value Target
Apple’s iOS is often praised for its security, but that very reputation makes it an attractive target for sophisticated threat actors. From high-profile individuals to governments, iPhones hold critical data, and hackers know it.
What Makes Zero-Click Exploits So Dangerous
Most malware requires you to click a suspicious link or download a sketchy app. Zero-click exploits? They need nothing. No clicks. No taps. Just silent, invisible infection, and you’re compromised without knowing a thing.
What Is Graphite Spyware?
Overview of Graphite
Graphite is an advanced piece of spyware designed to infiltrate and monitor iOS devices without the user’s knowledge. It’s capable of accessing photos, messages, microphone, camera, and real-time GPS location, all in stealth mode.
Who Developed It?
Although it’s hard to trace with absolute certainty, Graphite has been linked to state-sponsored groups and commercial spyware vendors. It’s built with precision, designed to exploit iOS with minimal traces.
Connection to Threat Actors
Analysts believe Graphite is either directly developed or heavily sponsored by intelligence agencies, given the level of technical sophistication and targeting strategy.
How Zero-Click Exploits Work
No Interaction Required
User doesn’t need to do anything to trigger the infection in Zero-Click Exploits. The attack might arrive via an iMessage, FaceTime call, or even a notification, and as soon as the message is processed by the system, the exploit executes.
How Devices Get Infected Silently
Graphite uses vulnerabilities in Apple’s message processing engines. As soon as a specially crafted message is received, it bypasses sandbox restrictions and executes malicious code.
Delivery Mechanisms
- iMessage rich text parsing bugs
- FaceTime vulnerabilities
- Push notification backdoors
- Exploitable code libraries within Safari or WebKit
Example of a Recent Attack
In one confirmed case, Graphite was deployed via a malicious iMessage sent to a journalist’s phone. The device was compromised before the message even appeared in the inbox.
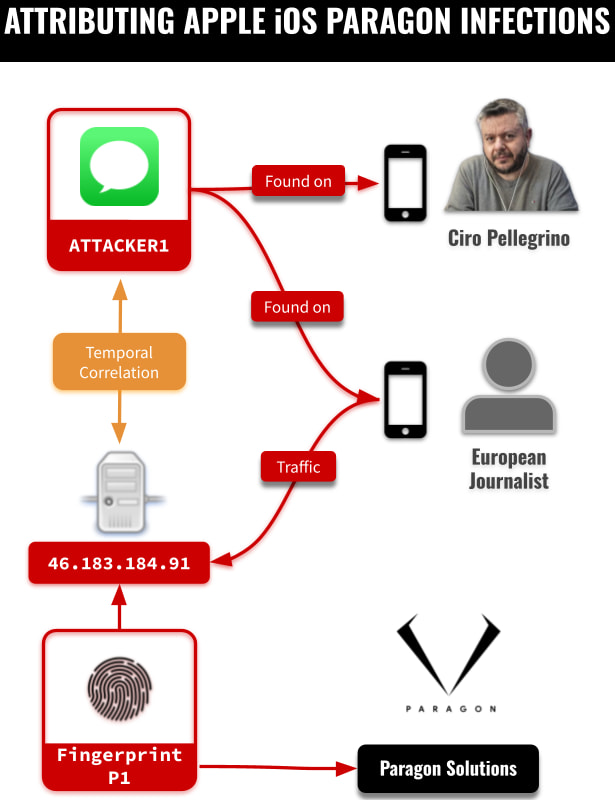
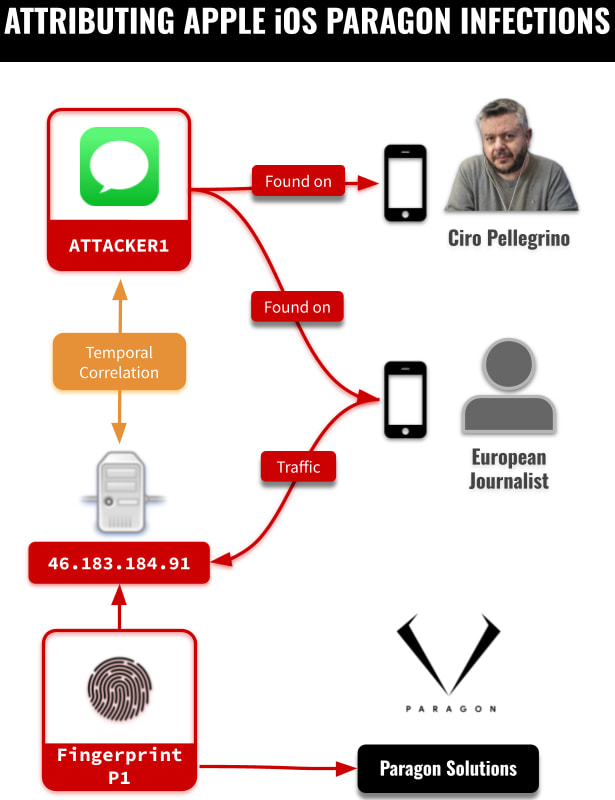
In early 2025, some iPhones were hacked without users even noticing. Citizen Lab found they were quietly connecting to a suspicious IP tied to the Graphite spyware, all while running iOS 18.2.1.
Graphite’s Attack Methodology
The iOS Vulnerability in Detail
Graphite exploited an unpatched flaw in iOS’s message handling system. The flaw allowed it to bypass Apple’s BlastDoor security mechanism, a sandbox meant to block malicious iMessages.
Payload and Execution
Once inside, Graphite installs a hidden surveillance module. It then:
- Connects to a command-and-control server
- Exfiltrates data silently
- Schedules future actions
- Deletes traces of its own activity
Exploiting Messaging Apps (e.g., iMessage)
iMessage is mostly the entry point due to its deep integration into iOS and the fact that it’s trusted by the system. Graphite crafted payloads that appeared as legitimate system data.
Persistence and Stealth
Graphite uses encrypted communication, disguises itself as system files, and maintains persistence even after restarts. Some versions even disable logging and forensics tools.
Who Is Being Targeted?
Journalists, Activists, and Diplomats
The victims are often those with sensitive roles: investigative reporters, political dissidents, human rights defenders, and government officials.
Government and Corporate Espionage
Graphite has also been detected in attacks against embassies, defense contractors, and global corporations, suggesting use in geopolitical cyberwarfare.
Regions Most Affected
High concentrations of attacks have been reported in:
- Middle East
- Southeast Asia
- Eastern Europe
- Parts of Africa and South America

Apple’s Response
Patch Releases and Mitigations
Apple moved quickly after initial reports, issuing security updates that patched the specific iOS vulnerability exploited by Graphite. These were included in emergency iOS updates (e.g., iOS 16.6.1 and above).
Official Statements and Warnings
Apple acknowledged the attack in a press briefing, stating it was “a highly targeted spyware campaign.” They emphasized that the average user was unlikely to be affected, though security researchers disagreed.
Why These Threats Keep Emerging
Despite Apple’s best efforts, new vulnerabilities continue to surface because:
- iOS is complex and ever-evolving
- Attackers are well-funded and persistent
- Users delay updates, leaving devices exposed
Protecting Yourself Against Zero-Click Threats
Keeping iOS Updated
Always run the latest iOS version. Apple’s security updates are your first and strongest line of defense.
Hardening Device Settings
- Disable iMessage or FaceTime if unnecessary
- Use Lockdown Mode (available in iOS 16+)
- Limit app permissions and background activity
- Avoid public Wi-Fi and unknown AirDrop connections
Using Security-Focused Tools
Tools like Mobile Verification Toolkit (MVT) from Amnesty International can scan your iPhone for signs of spyware. While not foolproof, they can detect known Graphite indicators.
What This Attack Reveals About Mobile Security
iOS’s Strengths and Weaknesses
iOS is secure, but not bulletproof. Zero-click exploits show that even top-tier platforms can be breached, especially when targeted by nation-state actors.
The Rise of Commercial Spyware
Graphite, Pegasus, Hermit, these tools are part of a growing ecosystem of commercial surveillance software sold to governments. Their use blurs the line between security and oppression.
Conclusion
The Graphite spyware campaign proves one chilling fact: you don’t need to click anything to be hacked anymore. For high-risk individuals, iPhones are no longer “unhackable.” Staying protected means staying informed, updating regularly, and using every available tool to defend your privacy. The future of mobile security depends not just on vendors like Apple, but on all of us staying one step ahead of the threats.
FAQs
What is a zero-click exploit?
A cyberattack that doesn’t require any user interaction, it infects the device automatically through bugs in background services.
Can I detect if I was infected?
It’s difficult, but forensic tools like MVT can help detect known indicators. Most infections go unnoticed without expert analysis.
What is Graphite’s origin?
While not officially confirmed, Graphite is believed to be developed or distributed by state-linked surveillance firms.
Has Apple closed the vulnerability?
Yes, Apple issued emergency updates to patch the flaw exploited by Graphite. Always install updates immediately.
How can I secure my iPhone from spyware?
Enable automatic updates, use Lockdown Mode, limit app permissions, and avoid suspicious links or messages.










